We all know OEMs recommend updating the BIOS version to ensure safety and take advantage of critical vulnerability fixes and feature enhancements with new BIOS versions. But the truth is… deploying a BIOS update is somewhat not encouraging, well… traditionally! On one hand, an interrupted installation can corrupt the BIOS and “brick” the PC, leaving it unable to boot and on the other hand, it’s a nightmare for our IT Administrators to create packages after packages with each version release, not to mention for the different number of system models that exist in an enterprise environment.
Another problem that has plagued IT Administrators is patching a BIOS that has an admin password configured. I know, WUfB delivers BIOS updates via UEFI capsule, which does not require entering the password to deploy the automatic update however this process lacks granularity and gives less control to an IT Administrator.
In this article, we will focus on to eliminate these pain points and truly aid IT Administrators who want to automate PC Lifecycle Management tasks such as BIOS Update. The objective here is to help you create / setup an evergreen package which will have quite a few Safety nets to avoid “brick” situation.
Let’s get started…
In this article, I will walk you through how to:
- Generate the secure BIOS password file and encryption key.
- Deploy the script to update BIOS to the recommended version.
- Deploy the script to update BIOS to the specified version.
The “Safety nets” in the script:
- If the device has USB drives attached, BIOS flashing process will be aborted.
- If the device is not connected to an external power source, BIOS flashing process will be aborted.
- If the device is not running Windows 10 1709 (Fall Creators Updated) and later, BIOS flashing process will be aborted.
- If the boot mode is not UEFI, BIOS flashing process will be aborted.
- If the script is running under 32-bit PowerShell, it will be re-launched automatically under 64-bit PowerShell.
- If the current BIOS version installed on the PC is same as the latest version available on the HP Software & Driver webpage, BIOS flashing process will be aborted.
PowerShell Script
Download the zip file (the .zip file contains):
- HP-BIOSUpdate.ps1 – script to update BIOS.
- Script and supporting files to generate a secure BIOS Setup Password file and corresponding AES encryption key – for customers who have set a unified BIOS Setup password across their fleet.
- AES.key
- Generate_SecurePassword.ps1
- Password.txt
Script Details
- The script will only run on HP manufactured devices and excludes virtual machines.
- You must run the script with Administrative privileges.
- Download the HP Client Management Script Library installer from https://www.hp.com/us-en/solutions/client-management-solutions/download.html and include the executable with the script.
- Ensure that .ps1 and .exe files are in the same folder.
- Logs are output to “C:\ProgramData\HP\CMSL\Logs<computername>_BIOSUpdate.log”
- BitLocker is suspended for one reboot to apply BIOS version upgrade, then BitLocker is re-enabled upon reboot.
- BIOS Flash is only supported on Windows 10 1709 (Fall Creators Update) and later.
- A UEFI boot mode is required for flashing, and legacy mode is not supported.
- Remove external drives such as USB memory keys, external Hard Disk drives, etc. if attached to the PC, else the script will exit gracefully.
- The script will exit without action if a BIOS password exists on a device but has not been specified in the script. If your devices share a unified BIOS password, you should use the enclosed “Generate_SecurePassword.ps1” script to generate a BIOS password file and corresponding AES encryption key to package with the BIOS update script. However, DO NOT call on the “Generate_SecurePassword.ps1” file in your “Install” Program in SCCM or any other Endpoint Management tool you prefer to deploy the PowerShell script.
- The script detects the following chassis types when checking for external power source:
- Notebook, Tablet
- Desktop, Tower, Workstation, Mini PC
- Small Form Factor, Convertibles
- AiO (All in One)
- PoS (Point of Sales)
- Expansion Chassis, Sealed Case PC
- See below table for the Standard Exit Codes Output by the PowerShell Script:
| Exit Code | Description |
| 0 | There is no error |
| 8 | Non-HP manufactured PC |
| 27 | OS version not supported |
| 64 | CMSL installer not found |
| 65 | CMSL install failure |
| 343 | General exceptions |
| 216 | BIOS password incorrect |
| 217 | BIOS download failure |
| 28 | USB drives attached |
| 29 | PC is not connected to AC power |
Deploying the Script to Update BIOS to the Latest Version
Some examples of Endpoint Management tools you can use to deploy the script are Microsoft System Center Configuration Manager, Microsoft Endpoint Manager, VMware Workspace ONE, Tanium, DesktopCentral, Altiris etc. In the Endpoint Management tool of your choice, create a device group for the targeted devices regardless if the BIOS version is outdated or latest and target the script to those devices. In production environment, the script can be run silently, but for purposes of this article, we are showing the script’s output when run in a command prompt. The script does the BIOS Update automatically, and you can run it periodically to enforce the BIOS Update across your fleet.
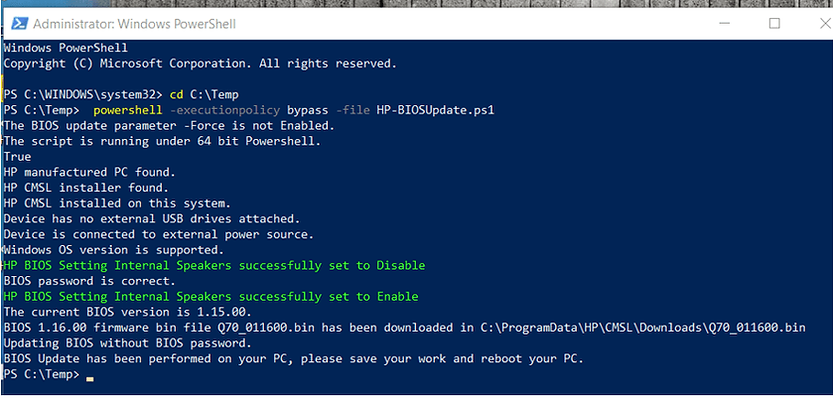
Generating the Secure BIOS Password File and Encryption Key
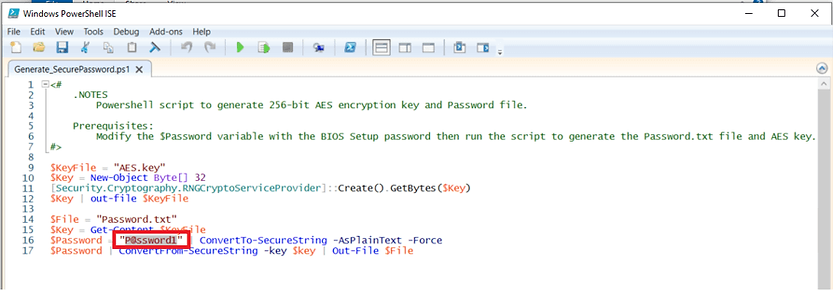
If you have set a unified BIOS Setup password across your fleet, run the included “Generate_SecurePassword.ps1” script to generate a secure password file and AES encryption key. This approach assumes that all devices share the same BIOS password.
- Enter the BIOS Setup password in the “Generate_SecurePassword.ps1” file. In this example, the password is “P@ssword1”
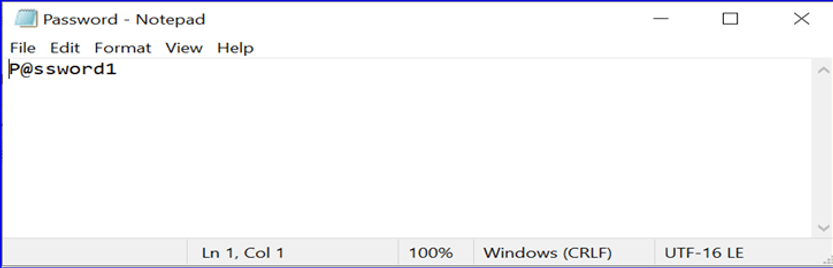
- Enter the same BIOS Setup password in the “Password.txt” and save the file.
- Run “Generate_SecurePassword.ps1” to generate a secure password.txt file and AES.key encryption key.
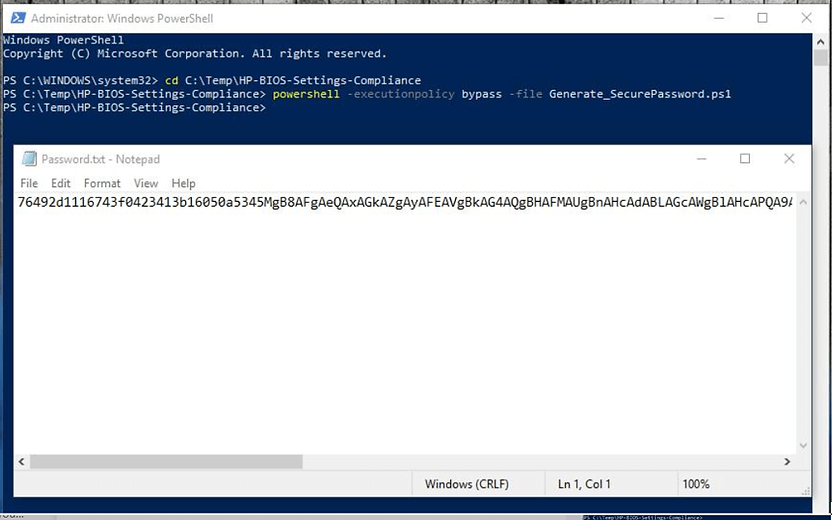
- Include both the “Password.txt” file and “AES.key” files along with the “HP-BIOSUpdate.ps1” script & the “CMSL installer” when creating a Package and deploying to your fleet.
[ OPTIONAL ]
Deploying the Script to Update BIOS to a Specified Version:
This section describes how to update BIOS to a specific version across your environment and this gives you more control in order to revert back the changes / downgrade the BIOS version.
The PowerShell script updates the fleet to the latest BIOS version if no parameter is specified. Use one of the following parameters if you need to Force update the BIOS to a specific version:
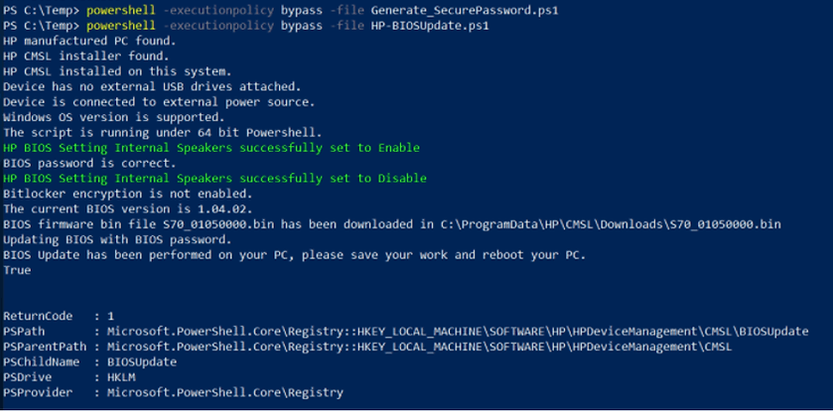
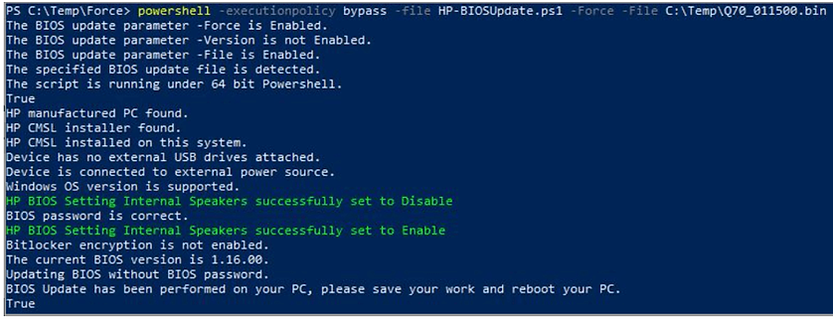
• -Force -File <BIOS update file path>
Updates the BIOS using the BIOS firmware file specified in the path. When using this parameter, the script will not download the firmware from the Internet and instead use the firmware in the specified path.
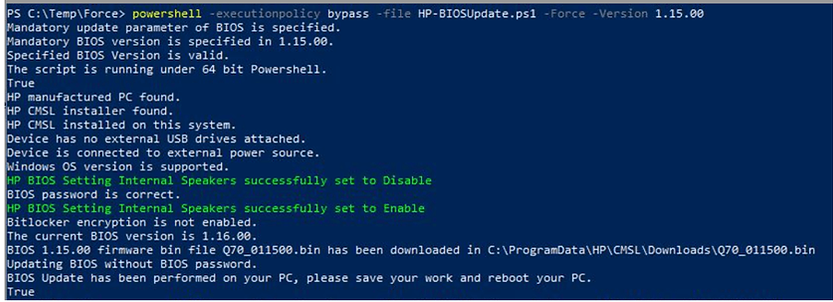
• -Force -Version <BIOS version>
Updates the BIOS to the BIOS version specified. When using this parameter, the script will download the firmware from the Internet.
Example of updating the BIOS with a specific BIOS firmware file:
powershell -executionpolicy bypass -file HP-BIOSUpdate.ps1 -Force -File C:\Windows\Temp\123.bin
Example of updating the BIOS to a specific BIOS version:
powershell -executionpolicy bypass -file HP-BIOSUpdate.ps1 -Force -Version 1.15.00
HP offers Proactive Insights powered by HP TechPulse, a powerful telemetry and analytics platform that provides all the actionable insights for the enrolled devices through a single, simple to use dashboard (SaaS application).
Using HP TechPulse, you can (among many other things)…
- Identify devices that have outdated BIOS versions using HP TechPulse and use this device list to target the deployment only to the ‘required’ devices that is running on outdated BIOS versions.
- Monitor the BIOS update status using an Excel report extracted from HP TechPulse.
- Monitor the BIOS updates status using the dashboard widget in HP TechPulse.
- Monitor the BIOS updates status using the missing BIOS update incidents automatically logged in HP TechPulse.
Additional Information:
- Detailed CMSL syntax available here
- HP CMSL Installer is available to download from HP Download Library
Please ensure you perform adequate testing before rolling out the script to your fleet.
* Please feel free to reach out with any comments or questions!
Related Posts
- Manage Battery Health Manager (BHM) Settings with HP CMSL
- Updating BIOS Version with HP CMSL
- Manage BIOS Settings with HP CMSL
- SCCM OSD – Domain Join Failed with Error code 0x54b on HP Elitebook 840 G8
- SCCM Device Collection Based on Computer Hardware Details | ConfigMgr
Subscribe to Techuisitive Newsletter
Be the first to know about our new blog posts. Get our newsletters directly in your inbox and stay up to date about Modern Desktop Management technologies & news.