Windows Autopilot group tags are used to categorize devices based on specific attributes. You can assign a group tag to a device during the autopilot registration or hash import. When you create rules using Autopilot device attributes, Autopilot devices that meet the criteria are automatically added to the group. This simplifies the device grouping during Autopilot device provisioning.
The group tag for individual devices can be updated from the Intune admin center. However, there are no such options available for bulk updates of group tags from the Intune admin center. We can use PowerShell and the Microsoft Graph API to bulk update group tags.
Microsoft Graph Command Line Tools
The users with the Intune Administrator role can update the group tag from the Intune admin console. However, you need access to Microsoft Entra ID Enterprise Application, Microsoft Graph Command Line Tools to update the Group tag through the Microsoft Graph API.
Application Name: Microsoft Graph Command Line Tools
API Name: Microsoft Graph
Claim Value:
- Group.ReadWrite.All
- Device.ReadWrite.All
- DeviceManagementManagedDevices.ReadWrite.All
- DeviceManagementServiceConfig.ReadWrite.All
- GroupMember.ReadWrite.All
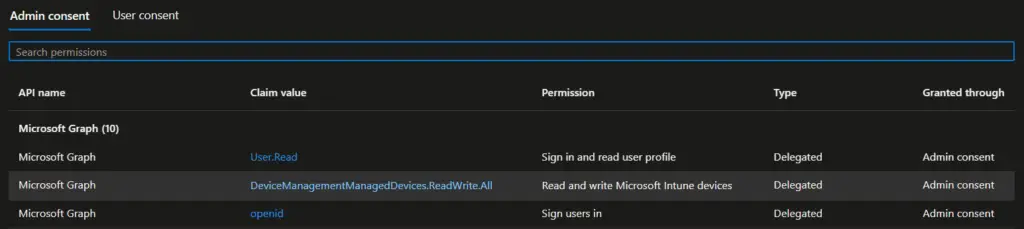
An Entra ID administrator must provide organization consent for the above API claim value. If admin consent has not been provided, you will see prompts below. The organization’s consent needs to be provided only once.
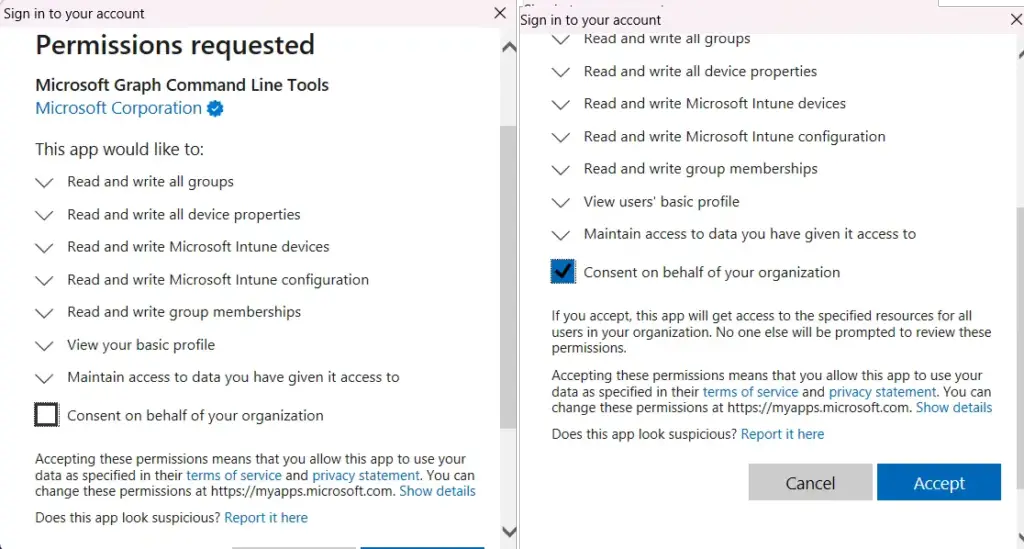
CSV File – Device & Group Tag Details
The PowerShell script takes input from the CSV file. You must organize the Device Name and Group tag in the below format in a CSV file. The column header must be the same as provided in the screenshot below.
The PowerShell Script
The below PowerShell script updates the group tag for all devices in the provided CSV file. You can also download the script & CSV file from the link provided at the end of this post.
The Microsoft.Graph.Intune and WindowsAutopilotIntune PowerShell modules are required for this script. If the required modules are not installed, then the script will install them.
Set-ExecutionPolicy -Scope Process -ExecutionPolicy RemoteSigned
$deviceList = "$PSScriptRoot\devices.csv"
#Install Microsoft.Graph.Intune module
if(-not (Get-Module Microsoft.Graph.Intune -ListAvailable))
{
Write-Host "Installing Microsoft.Graph Module" -ForegroundColor Cyan
Install-Module Microsoft.Graph.Intune -Scope CurrentUser -Force
}
#Install WindowsAutopilotIntune module
if(-not (Get-Module WindowsAutopilotIntune -ListAvailable))
{
Write-Host "Installing WindowsAutopilotIntune Module" -ForegroundColor Cyan
Install-Module WindowsAutopilotIntune -Scope CurrentUser -Force
}
Connect-MgGraph -scopes Group.ReadWrite.All, Device.ReadWrite.All, DeviceManagementManagedDevices.ReadWrite.All, DeviceManagementServiceConfig.ReadWrite.All, GroupMember.ReadWrite.All
$devices = import-csv -Path $deviceList
$totalDevices = ($devices).Count
$sn=1
Write-Host "Total Devices: $totalDevices" -ForegroundColor Yellow
foreach ($device in $devices){
try
{
$serialNumber = $device.SerialNumber
$groupTag = $device.GroupTag
Write-Host -NoNewline "Device:$sn of $totalDevices, Serial Number:$serialNumber, Group Tag:$groupTag ....." -ForegroundColor Cyan
$id = (get-AutopilotDevice -serial $serialNumber).id
Set-AutopilotDevice -id $id -groupTag $groupTag
Write-host "Group tag udpated." -ForegroundColor Green
}
catch
{
$message = $_.Exception.Message
Write-Host "Error: $message" -ForegroundColor Red
}
$sn+=1
}
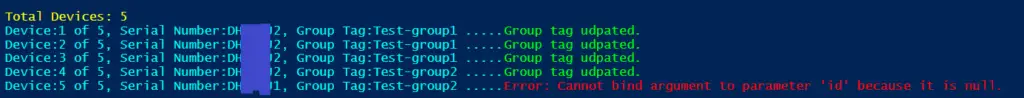
Script Download
You can download the PowerShell script and sample CSV file from the link below.
Related Posts
- Powershell – Get System up time
- Powershell Script : List AD Organizational Unit and GPOs linked to them
- Powershell – Compare hardware and software details on two computers
- Powershell Script : Retrieve AD Computers Properties
- Powershell – Merge CSV files & Insert file name as a column
- Powershell Script: Validate if Computer account exists in Active Directory
- Powershell remote – WinRM cannot complete the operation
- Powershell script to Add bulk users / computers to AD Group
- PowerShell Script : Copy AD Group Membership
- Using PowerShell Behind a Proxy Server
Subscribe to Techuisitive Newsletter
Be the first to know about our new blog posts. Get our newsletters directly in your inbox and stay up to date about Modern Desktop Management technologies & news.