Microsoft Intune includes Endpoint security policies that you can use to secure your device and mitigate the risks. The Endpoint security blade lists all the tools available through Endpoint Manager that you will use to keep devices secure. In this blog post, we will discuss how to block USB device access using Microsoft Intune Device Control settings. We will also discuss how to manage exceptions so users with genuine business needs can still access USB media.
Create Azure AD Groups
We will create two Azure Active Directory (AAD) groups to block USB device access and allow exceptions to devices when users have genuine business need.
- All Windows 10/11 Devices: We will use this group to deploy the USB Device Control policy on all Windows 10/11 devices.
- USB Device Restrictions – Exception: We will use this group to provide a temporary or permanent exception to user by adding their devices to AD group.
Create both groups from Endpoint Manager admin center | Groups blade.
Group 1 :
Group Type: Security
Name: All Windows 10/11 Devices
Membership Type: Dynamic Devices
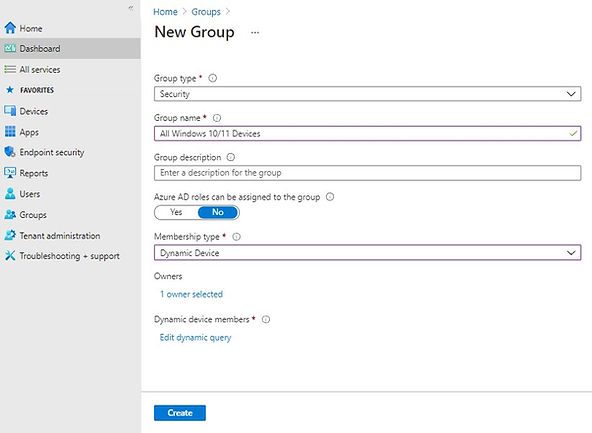
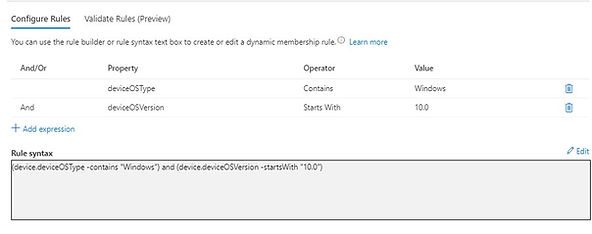
Dynamic membership rule:
(device.deviceOSType -contains "Windows") and (device.deviceOSVersion -startsWith "10.0")
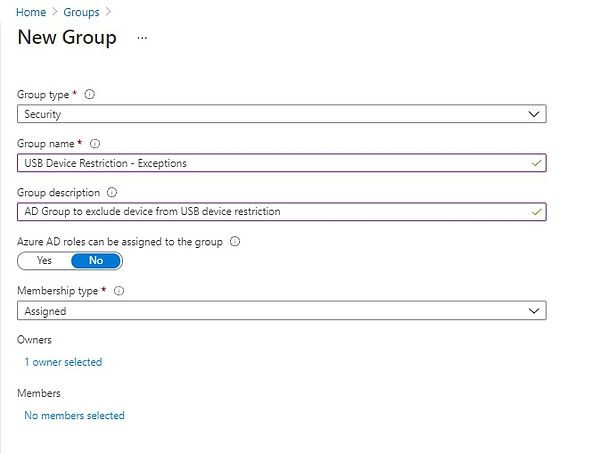
Group 2:
Create second Group USB Device Restrictions – Exception with the details in below screenshot. We are not adding any members in this group as of now.
Group Type: Security
Group Name: USB Device Restriction – Exceptions
Membership Type: Assigned
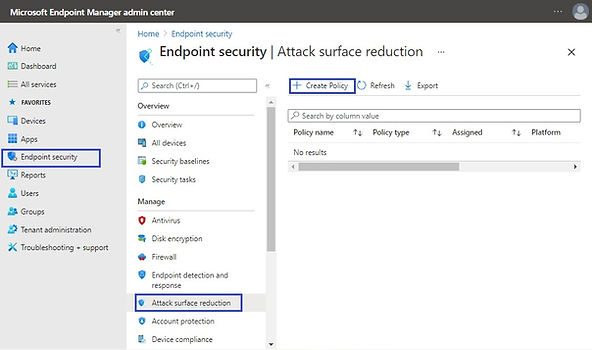
Create a Device Control Policy to Block USB Device Access
We will now create a Device control policy to deploy settings on Windows 10 / 11 devices. The device control policy will block USB device access once it’s applied to a device.
To create a Device control policy, Go to Microsoft Endpoint Manager admin center and select Endpoint security | Attack Surface reduction | Create policy
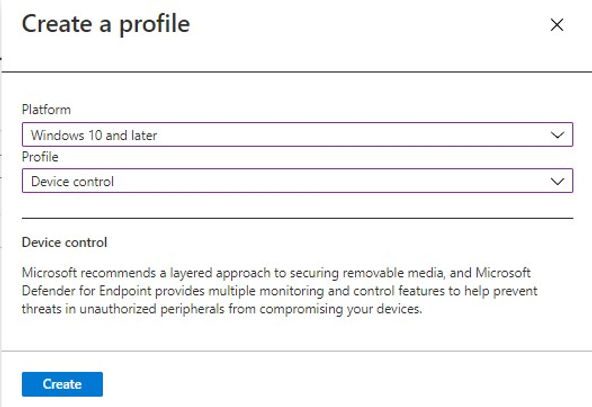
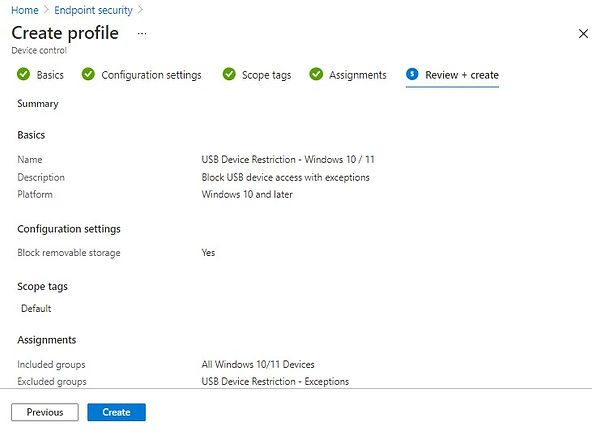
Select the following details in Create a profile pane and click on Create.
Platform: Windows and later
Profile: Device control
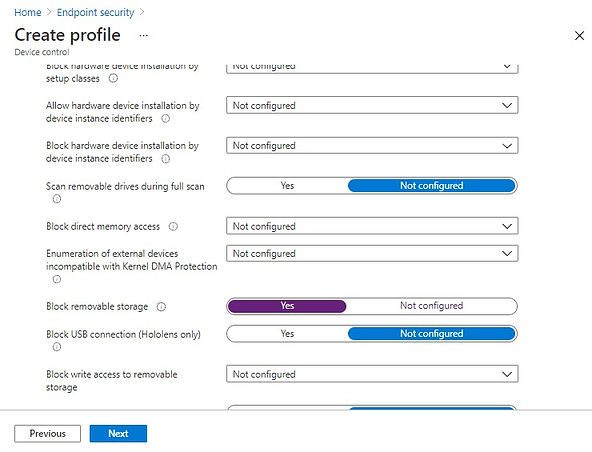
In the Configuration settings tab, set Block removable storage setting to Yes and click on Next
Apply the scope tags in next screen if applicable, else click on Next to got to Assignments tab.
Add All Windows 10/11 Devices AAD group in the Included groups section.
Add USB Device Restriction – Exception AAD group in the excluded groups section.
Click on Next.
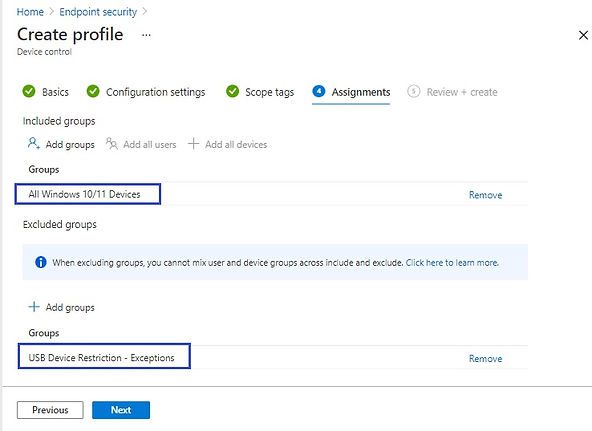
In the Review + create tab, review the settings and click on Create to complete profile creation process.
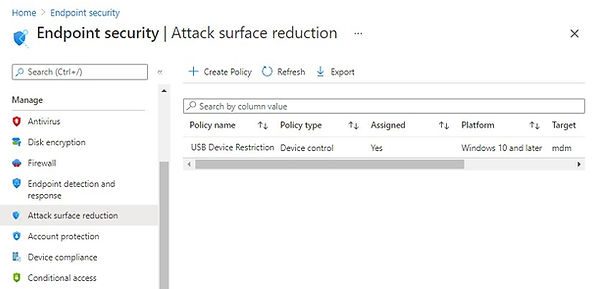
You can validate profile from Endpoint security | Attack surface reduction blade.
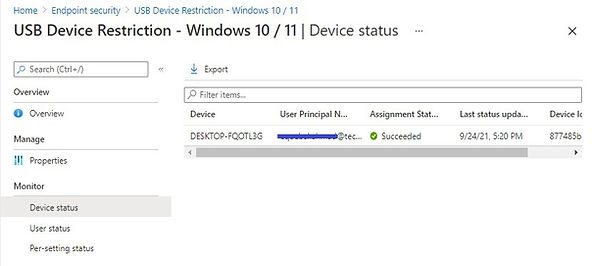
Force policy sync on your test device and check the policy Assignment Status after some time. The policy has been successfully applied now.
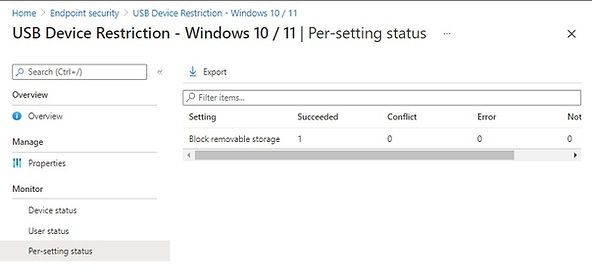
You can also validate the per-setting status if you have added multiple settings in the same policy.
End User Experience
Once the policy successfully applied, a user would not be able to access the USB media. The following error will be shown when the user tries to access USB media.
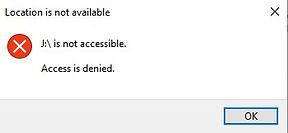
End User Experience After Applying Exception
To exclude a device from the USB block list, the user device needs to be added to the AAD group that we created in the beginning.
Go to Endpoint Manager | Groups and select USB Device Restriction – Exceptions Group and select Members.
Click on Add Members to add the device to Azure AD Group.
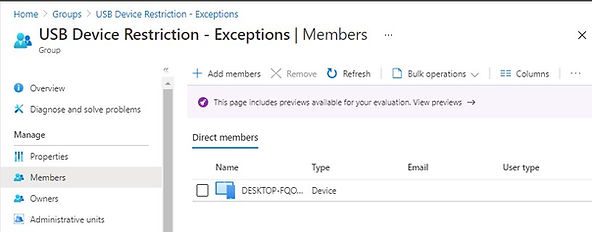
Once the policy is refreshed on the client, the user can access the USB device. We have added the same device in the exception where USB was blocked.
Manage exceptions through Azure AD Group
As an MEM | Intune administrator, your responsibility should be limited to the policy implementation. Since the exception management for this policy will be an ongoing activity, this needs to be carefully planned and handed over to lower support tiers or location leads.
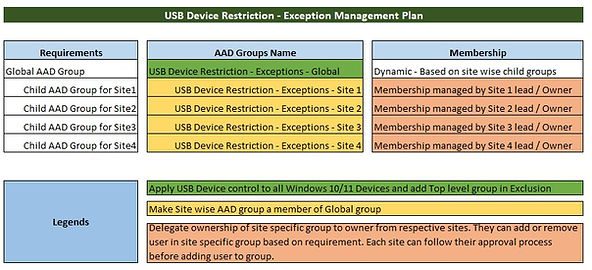
Here is a simple plan which you can use to delegate the group membership. A global AAD group will be used for policy exclusion and a child group for each site ( This can be departments, business units, etc. based on your requirements) will be added to global group membership. The child group owner will be from the local site who can validate user exception requests and add the user to their site-specific exceptions group.
See the illustration in the below screenshot.
Related Posts
- Block USB Device Access with Exceptions | Microsoft Intune
- Deny Write Access to USB Devices Using Intune Catalog Settings
- Manage Windows Local Administrator Password with Intune & Windows LAPS
- Check OS Version Compliance with Device Compliance Policy & Notify User | Microsoft Intune
- How to manage the local administrators group on Azure AD joined devices | Intune
Subscribe to Techuisitive Newsletter
Be the first to know about our new blog posts. Get our newsletters directly in your inbox and stay up to date about Modern Desktop Management technologies & news.