Overview
Windows Autopatch is a cloud-based service built into Microsoft Intune that automates the deployment of updates for Windows, Microsoft 365 Apps, Edge, and Teams. It streamlines patch management through phased deployment rings and centralized monitoring.
Even with automation, proactive monitoring and troubleshooting remain essential. Intune equips admins with dashboards, alerts, diagnostic tools, and Graph API/Copilot capabilities to detect issues early and resolve them swiftly. In this post, you’ll find detailed, actionable guidance to monitor your Autopatch environment effectively and fix common pitfalls.
Step-by-Step Guides to Troubleshoot Windows Autopatch Issues
1. Check Windows Autopatch Device Readiness Status
Windows Autopatch device readiness refers to ensuring that your organization’s devices meet all the requirements necessary for successful management and updates by the Windows Autopatch service. The device must be in the Ready state for receiving the updates.
The Windows Autopatch Devices Readiness report is accessible from the Device / Monitoring / Autopatch Groups Membership. This report provides the status of Windows autopatch device readiness. You can determine whether a device is Ready, Not Ready, ot Not registered to Autopatch service.
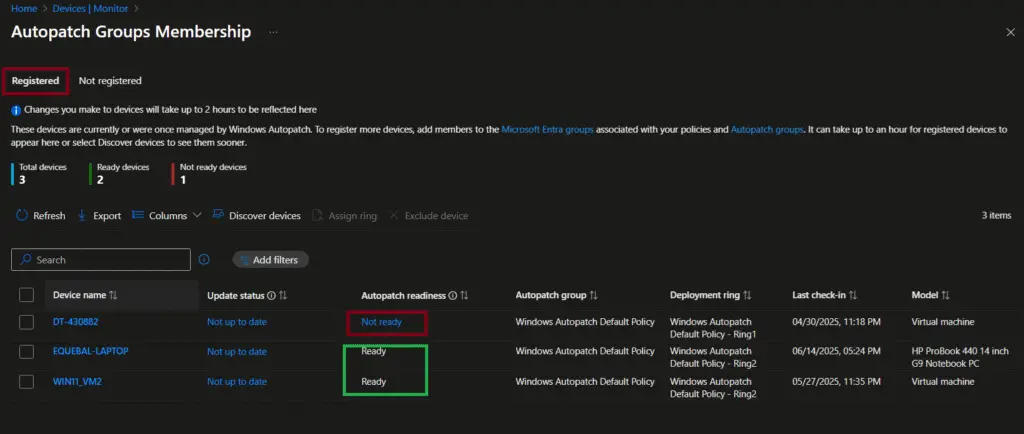
Device with Registered > Ready status
In a Windows Autopatch readiness report, the “Ready” status indicates that a device meets all requirements to be fully managed by the Autopatch service. This means the device has passed both prerequisite checks (before registration) and post-registration readiness checks, ensuring it can receive and report software updates without issues. The report also includes the name of the Deployment ring that you can refer to understand which ring the device is a member of.
Device with Registered > Not ready status
Devices that are Not ready may have configuration mismatches, missing updates, or other issues that prevent them from being fully managed by Autopatch. IT admins can use the readiness report to detect and fix these problems
The possible issues are listed below. I have added the screenshot for the issues that I encountered during the autopatch testing.
- The device has not synchronized with Intune for the past 28 days:
Quick Checklist: Device not synced with Intune (28+ days)
- Power on the device and connect to the internet
- Trigger manual sync: Settings > Accounts > Access work or school > Sync
- Run
dsregcmd /statusto confirm the join state - Check the Intune portal for stale records and clean up if needed
- Verify firewall/VPN allows Intune service endpoints
- Re‑enroll the device if sync still fails
- Conflicting Windows Update for Business settings:
Conflicting Windows updates for business settings may prevent devices from being registered with the Autopatch service. You need to ensure these settings are configured through GPO or Microsoft Intune.
Alternatively, you can also use Windows Autopatch – Auto remediation script to fix the conflicts. The script can be deployed as an Intune remediation script.
You may see the following errors in case of a conflict when selecting the ‘Not Ready” link in the Autopatch readiness report.
Error description: Windows Autopatch has identified a configuration that will prevent the device from receiving Windows updates, drivers, and firmware.
Registry keys: Software\Policies\Microsoft\Windows\WindowsUpdate\AU\NotAutoUpdate
Error description: Windows Autopatch has identified a configuration that will prevent the device from receiving Windows updates, drivers, and firmware.
Registry keys: Software\Policies\Microsoft\Windows\WindowsUpdate\DoNotConnectToWindowsUpdateInternetLocations
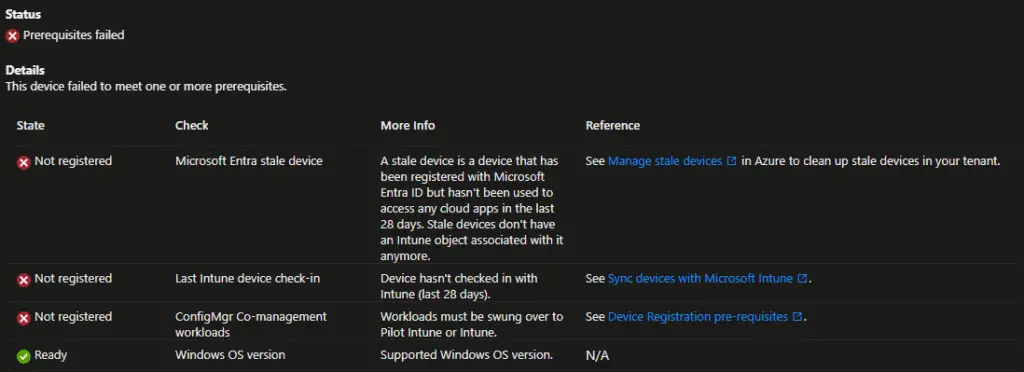
Device with Not registered status
The Not Registered tab displays details of devices that haven’t met the prerequisites for Windows Autopatch registration.
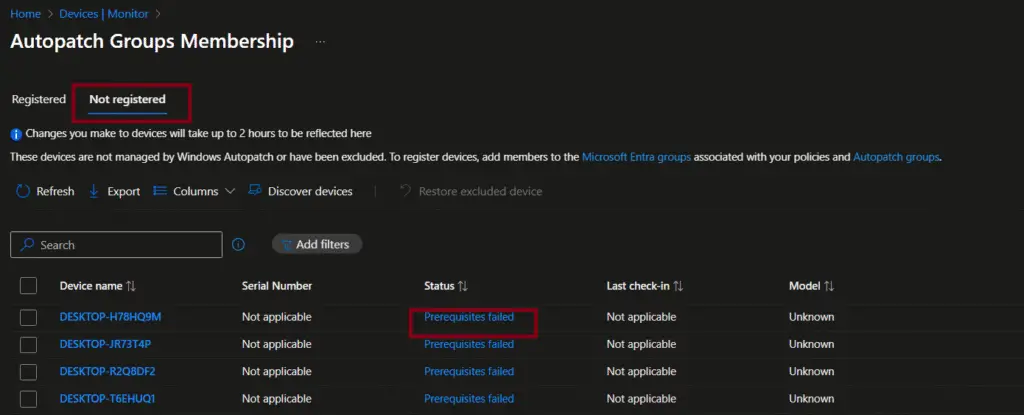
The prerequisites include the following checks:
- Intune or Cloud-Attached
- Microsoft Entra stale device
- Windows OS version
- ConfigMgr Co-management workloads
- Microsoft Entra ID join type
- Disabled Microsoft Entra device
- Empty Device Serial Number
- Empty Device Manufacturer
- Empty Device Model
- Duplicated Serial Number
- Last Intune device Check-in
Now, take a look at the following prerequisite issues that I encountered during Windows autopatch implementation. I have added screenshots for your reference.
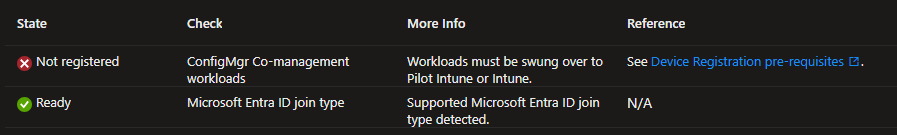
Check: ConfigMgr Co-management workloads
More info: Workloads must be swung over to pilot Intune or Intune.
The screenshot below shows that the device is a Co-managed device. However, the Windows update workload has not been swung over to Intune.
Ensure you have added the device to the appropriate collection in Configuration Manager to switch the workload to Intune. The device must be connected to the corporate network (office, VPN, or CMG) to allow the latest Configuration Manager policy downloads.
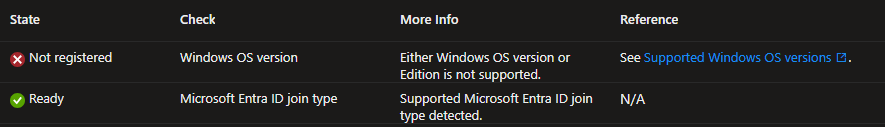
Check: Windows OS version
More Info: Either Windows OS version or Edition is not supported
The screenshot below shows that the device doesn’t meet Windows OS version prerequisites. Please check Windows Autopatch Prerequisites to know about supported OS versions.
Check: Microsoft Entra stale device
More Info: A stale device is a device that has been registered with Microsoft Entra ID but hasn’t been used to access any cloud apps in the last 28 days. Stale devices don’t have an Intune object associated with it anymore.
Another example where the device failed multiple prerequisites check. The workload has not been swung to Intune. However, the device has also not reported to Intune or Entra ID for more than 28 days. Hence, it may be a stale record, or the user may be on a long vacation.
If you’re seeing a large number of stale devices in Entra ID, it may indicate that a proper device decommissioning process is missing in the environment.
You can check Detailed prerequisite check workflow diagram at Microsoft Learn for more details about autopatch device registration prerequisites.
2. Check Policy Conflicts and Errors
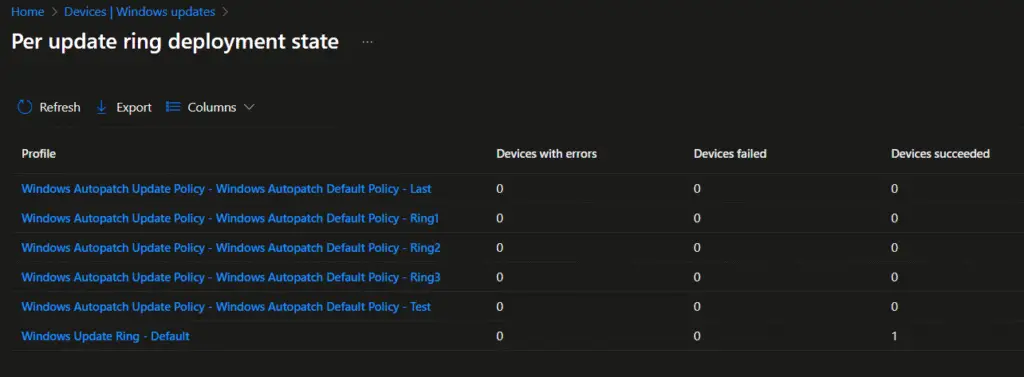
The Deployment status report—accessible via Devices → Windows Update → Monitor—lets you monitor policy conflicts and errors across every Windows Autopatch update ring (e.g., Test, First, Fast, Broad, Last). It presents a device‑by‑device breakdown showing the assigned deployment ring, update state (such as Succeeded, Error, In Progress, Conflict), and whether the update has been paused. Clicking on a specific ring or policy name drills down into detailed logs, highlighting the root causes of conflicts or failures, such as WSUS/GPO interference, missing prerequisites, or diagnostic errors. Optional columns like hex error codes, client/service state, and last Intune check-in time provide added context for in-depth troubleshooting. This centralized view simplifies identifying problem devices, analyzing failure reasons, and prioritizing remediation
3. Check Software Updates Reports
The Microsoft Intune admin center features a robust suite of Windows update reports, accessible under Devices → Windows updates. These reports provide both high-level overviews and granular device-level insights into update deployment:
Compatibility & Readiness Insights – The Feature Update Device Readiness report provides risk assessments for each device, highlighting possible compatibility barriers from apps, drivers, or system configurations.
Update Rings Report – Displays deployment results (Succeeded, Error, Conflict, Not Applicable, In Progress) for each update ring policy, showing device counts and status percentages in intuitive charts.
Device-Level Reporting – Drilling into a specific ring reveals detailed data per device, including check-in timestamps, user, individual setting statuses, and full policy assignment results.
Feature Updates Reporting – Enables compliance tracking and failure troubleshooting for feature updates, with dedicated “Organizational” and “Operational” views and alert-level detail.
Driver & Expedited Update Reports – Specialized reports surface driver update failures and expedited quality update issues, allowing targeted triage.
Windows Autopatch Issues – Cause vs Resolution – Quick Comparison Table
| Issue | Cause | Resolution |
|---|---|---|
| Device not synchronized with Intune for past 28 days | Device inactive, powered off, or stale record in Entra ID/Intune. VPN/firewall blocking sync. | Power on and connect device, trigger manual sync, run dsregcmd /status, clean stale records, verify firewall/proxy, re‑enroll if needed. |
| Device shows “Not Ready” in Autopatch readiness | Missing prerequisites (unsupported OS, stale hybrid join, conflicting GPOs). | Verify OS version, run readiness report, migrate GPOs to Intune, remediate conflicts, ensure licensing compliance. |
| Device shows “Not Registered” | Enrollment prerequisites failed (unsupported edition, stale Entra ID record, hybrid join issues). | Update OS edition, clean stale records, re‑enroll device, confirm prerequisites before retry. |
| Policy conflicts detected | Overlapping GPOs vs Intune policies, duplicate settings applied. | Run gpresult /h report.html, identify conflicts, migrate policies to Intune, remove redundant GPOs. |
| Software updates not applying | WSUS/GPO conflicts, Windows Update service disabled, VPN blocking update endpoints. | Ensure workloads are managed by Intune, check Windows Update service status, validate firewall/proxy, re‑sync device. |
| Stale or orphaned devices in Intune/Entra ID | Devices no longer active but still listed, hybrid join cleanup not performed. | Regularly audit device inventory, remove stale records, automate cleanup via Graph API. |
| Licensing or role assignment issues | Missing required licenses (E3/E5), RBAC misconfiguration. | Assign correct licenses, verify RBAC roles, confirm Autopatch service account permissions. |
Frequently Asked Questions on Windows Autopatch Troubleshooting
Q1. What does “Not Ready” mean in Windows Autopatch?
It indicates that the device does not meet one or more prerequisites (e.g., unsupported OS version, stale Entra ID record, or conflicting GPO settings).
Q2. How do I fix policy conflicts in Intune Autopatch?
Run gpresult /h report.html to identify conflicting GPOs, then migrate those settings into Intune configuration profiles.
Q3. Why is my device showing “Not Registered”?
This usually happens when prerequisites fail during enrollment. Common causes include hybrid-joined devices with stale records or unsupported editions of Windows.
Q4. Can I monitor Autopatch readiness via Microsoft Graph?
Yes. You can query Autopatch readiness reports using Graph API endpoints, which allows automation and integration with dashboards.
Q5. How often should I check Autopatch readiness reports?
Best practice is weekly, especially before Patch Tuesday, to ensure devices are compliant and update rings are healthy.
By embracing Windows Autopatch, organizations can achieve a more secure, efficient, and hands-off approach to managing their Windows and Microsoft 365 updates. It’s a powerful step towards modernizing your IT operations and ensuring your workforce always has access to the latest, most secure tools.
Related Posts
- Understanding Windows Autopatch with Intune
- Manage Edge Chromium favorites with Endpoint Manager | Intune
- Configure Edge Chromium Homepage & Startup Page
- Configure Microsoft Edge Sleeping Tabs using Intune
- Configure Google Chrome settings using Administrative templates | Intune | Endpoint Manager
- Block USB Device with Exception
- Deny Write Access to USB Devices Using Intune Catalog Settings
- Manage Windows 10 /11 Desktop Wallpaper with Microsoft Intune
- Manage Local Admin Password with Intune & Windows LAPS
- How to Create a Custom RBAC Role in Intune for LAPS Password Administrator
Subscribe to Techuisitive Newsletter
Be the first to know about our new blog posts. Get our newsletters directly in your inbox and stay up to date about Modern Desktop Management technologies & news.