Windows Local Administrator Password Solution (LAPS) from Microsoft allows you to manage and rotate local administrator passwords on Windows devices. A custom RBAC role in Intune is required if you want to delegate password administration to help desk members. The password administration for Windows LAPS includes retrieving the password for a Windows device from the Microsoft Intune console and rotating the password for a device based on requirements.
Let’s go through the below post to understand the steps required to delegate LAPS password administration to IT help desk by creating a custom Role Based Access Control (RBAC) role.
Create Azure AD Group
An Azure AD group is required to simplify the Intune RBAC roles. The user who needs to work on Windows LAPS password administration can be simply added to this AAD group to get all necessary access. Follow the below steps to create an Azure Active Directory group.
- On the Azure portal, go to Azure Active Directory > Groups and click on New Group
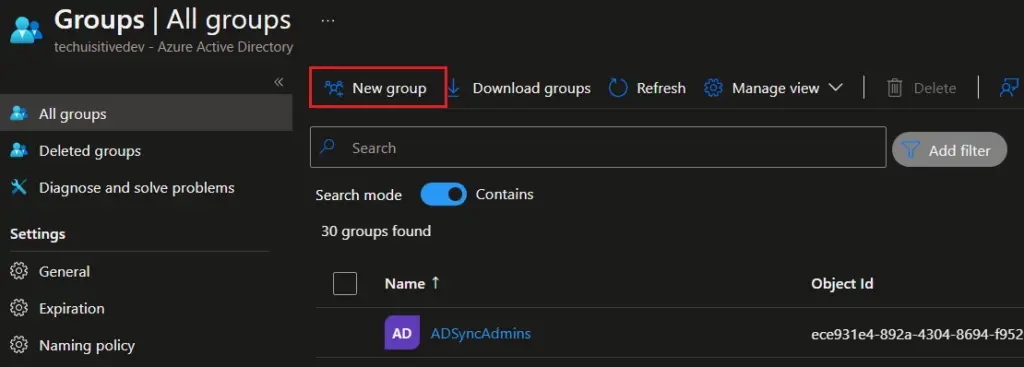
- On the New Group page, provide the following details.
- Group Type : Security
- Group Name: Provide group name as per your organization naming standards
- Azure AD roles can be assigned to the group : Select Yes.
- Membership Type: Assigned
- Members: Add the user if you want to add any at this point of time.
Click on Create to create AAD group.
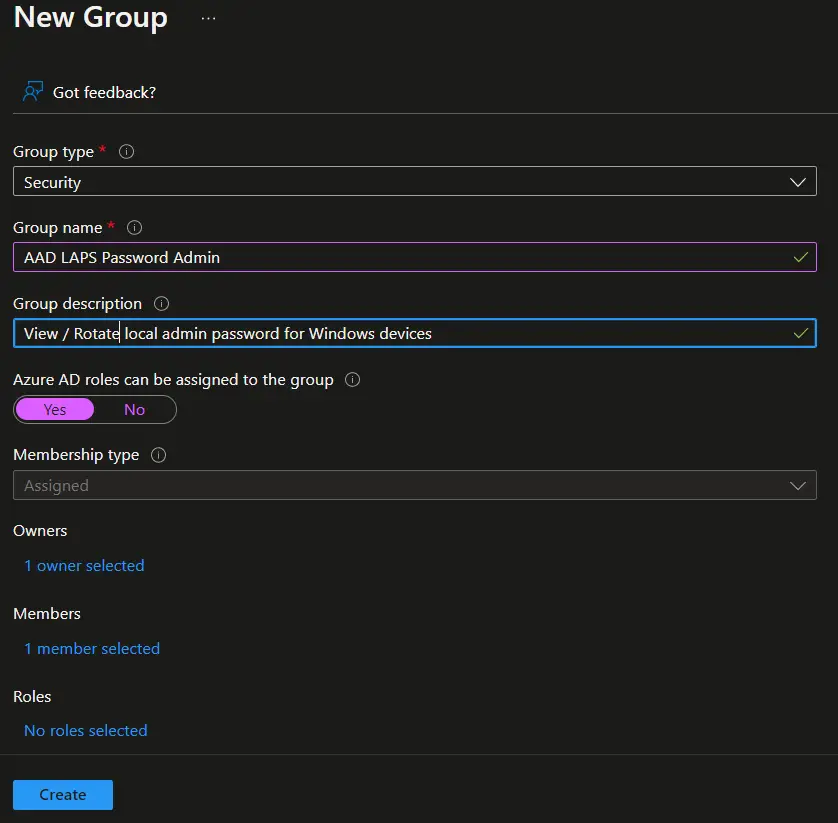
- Click Yes on the message box.
Create Azure RBAC Custom Role to View password
The next step is to create a custom AAD role to view Windows LAPS password. As of now Windows LAPS is in preview and no built-in role available in Azure AD for this. To view password details, your account must have one of the following Azure Active Directory permissions:
microsoft.directory/deviceLocalCredentials/password/readmicrosoft.directory/deviceLocalCredentials/standard/read
Follow the below steps to create a custom RBAC role in Azure AD.
- On the Azure portal, navigates to Azure Active Directory > Roles and administrators , and click on “New custom role“
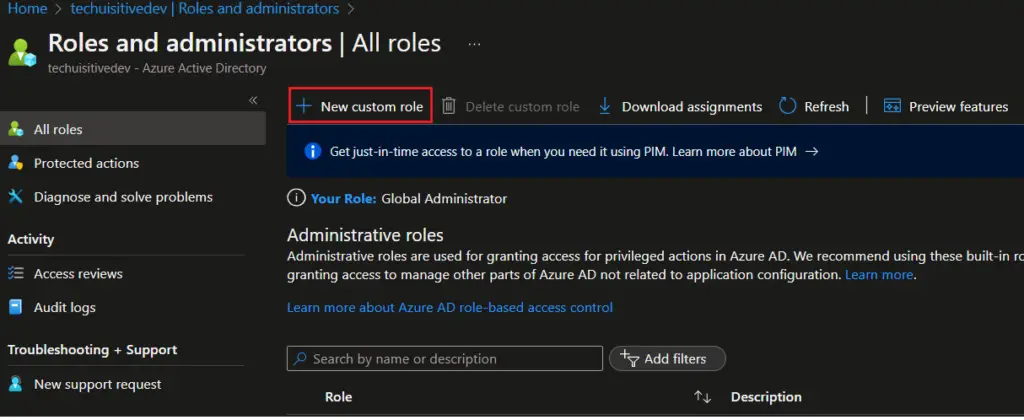
- On the next page, provide role name, description and click on Next.
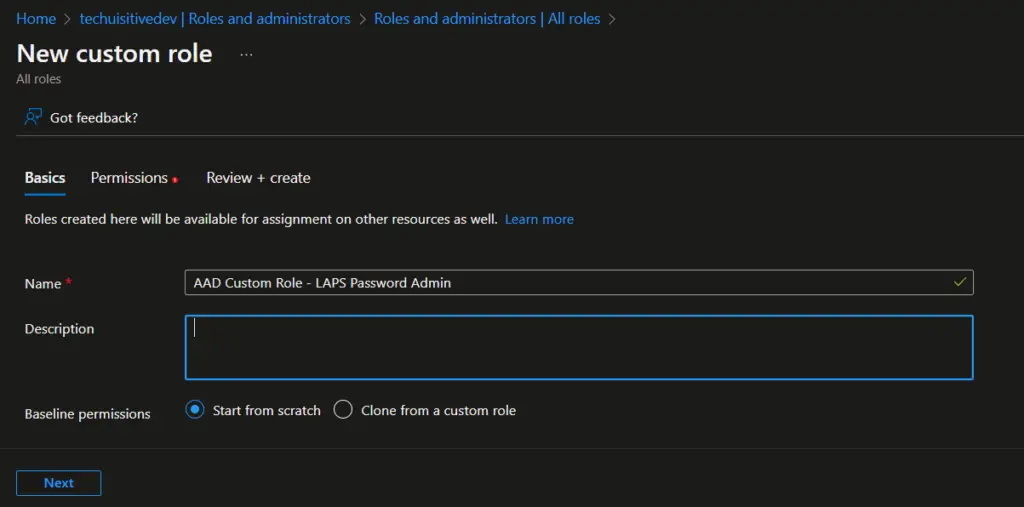
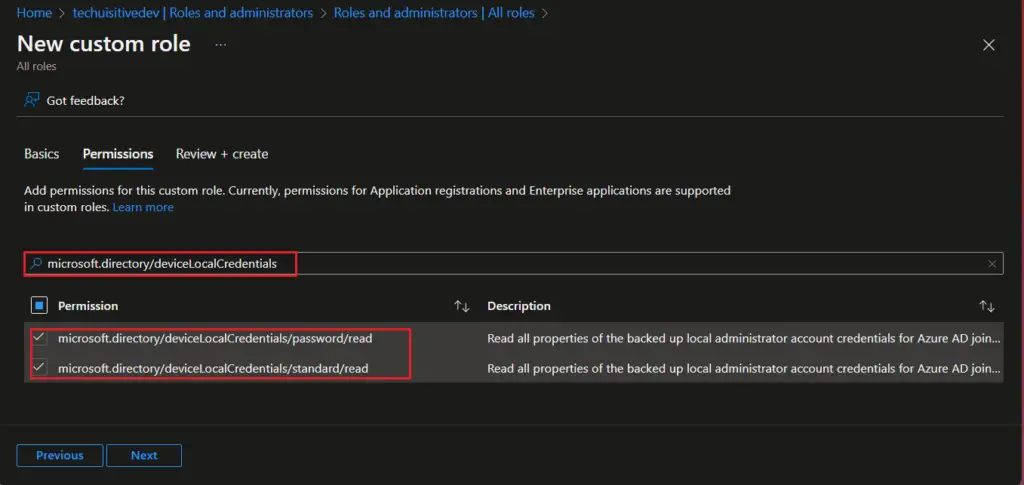
- On the Permission page, search for
microsoft.directory/deviceLocalCredentialsand select the permissions from the result.
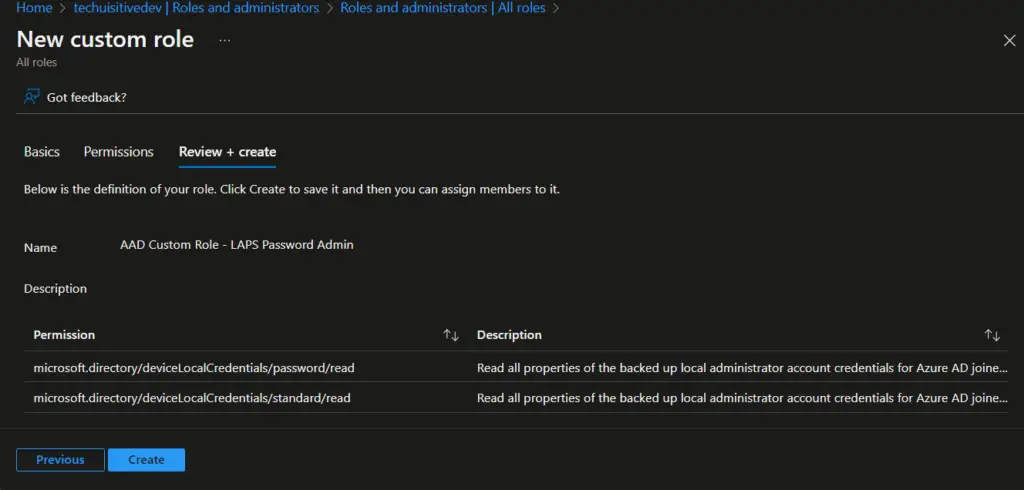
- On the Review + create page, review the details and click on Create.
Assign Azure AD Custom Role
We have created an Azure AD custom role in the last step. Now this role needs to be assigned to Azure AD Group which we created earlier.
- On the Role and Administrator page, search for AD group you created for LAPS and click on the group.
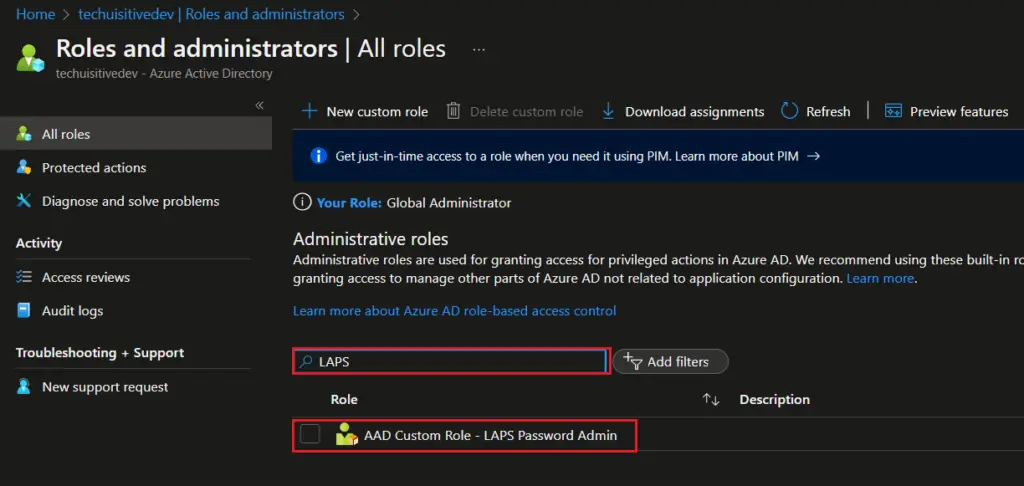
- Click on Add Assignments.
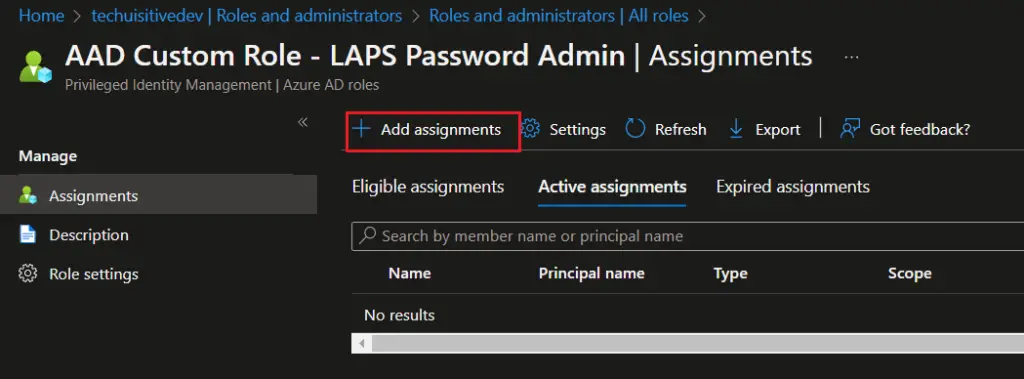
- On the Add assignments > Membership, select the following.
- Scope type : Directory
- Select members : Select the AAD group you created for LAPS password administrators.
- Click on Next
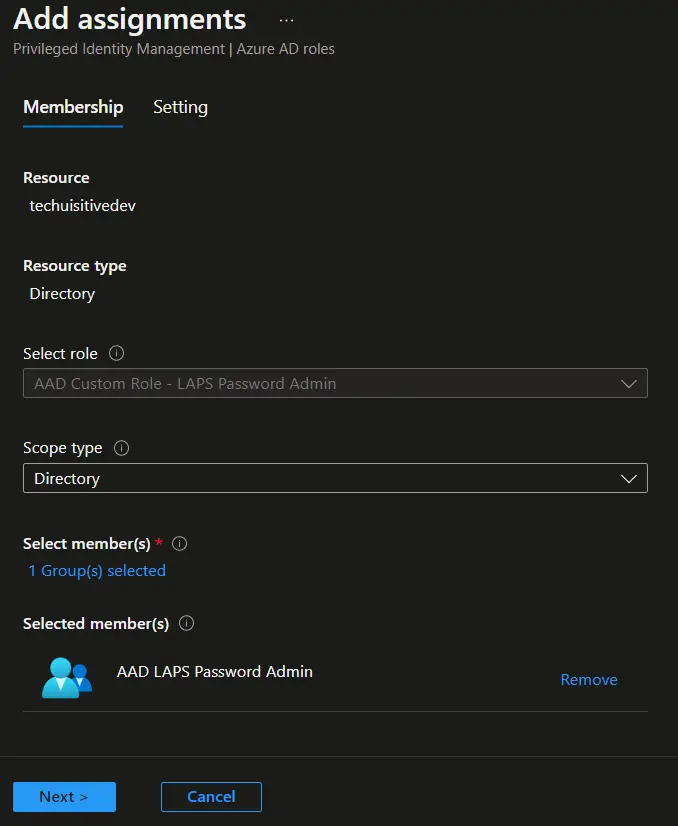
- On the Add assignments > Settings page, select Active in Assignment type, provide the justification, and click on the Assign button.
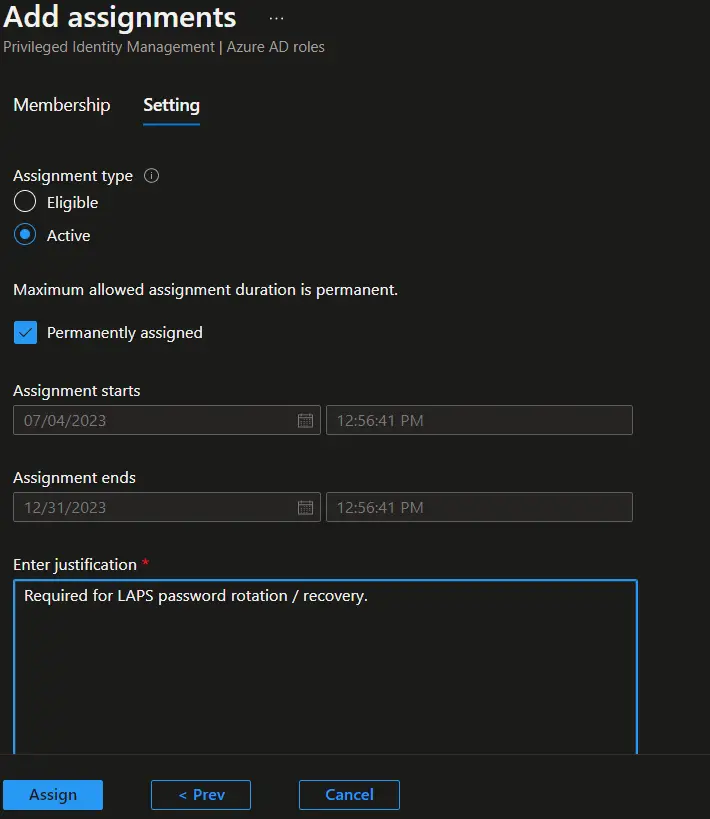
- The role is now assigned to the AAD group. You can see the details in the Assignment blade.
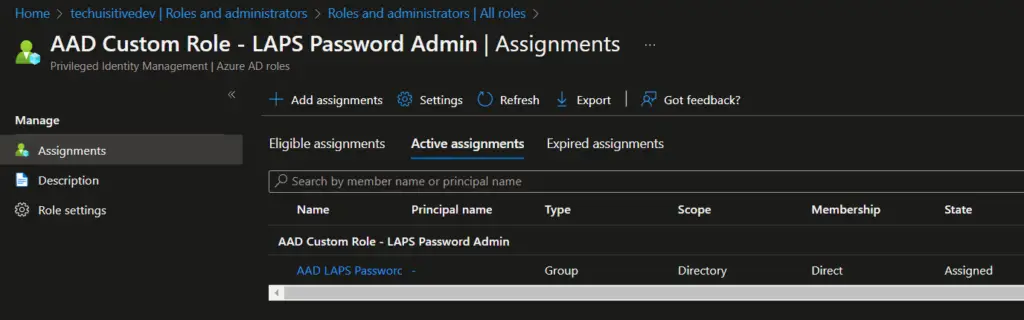
Create Custom RBAC Role in Intune for LAPS Password Administration
We will now create a custom RBAC Intune role for LAPS password administration. This role allows user to access “Local Admin Password” blade for a device, view and rotate local admin password.
- On the Microsoft Intune admin center, navigate to Tenant administration > All roles and click on Create
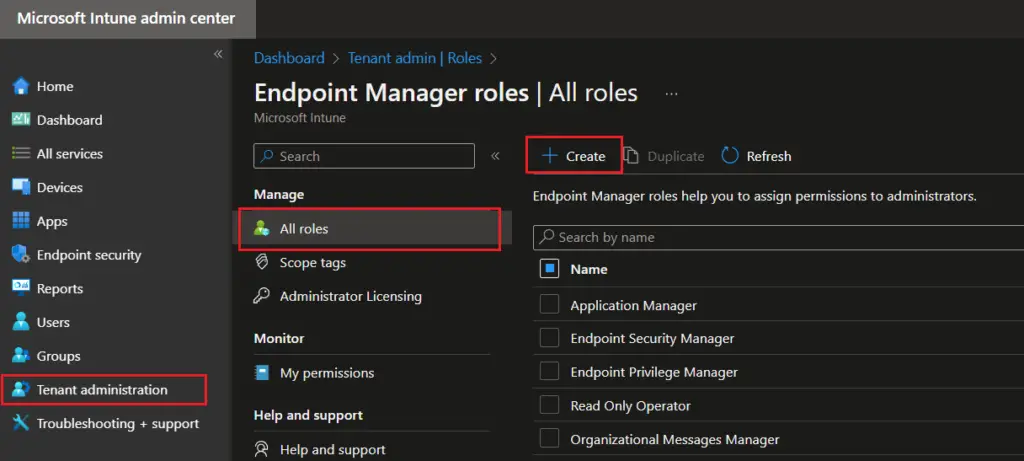
- On the Basic page, provide the profile name and description for Intune rbac roles. click on Next.
- On the Permission page, select the following permissions.
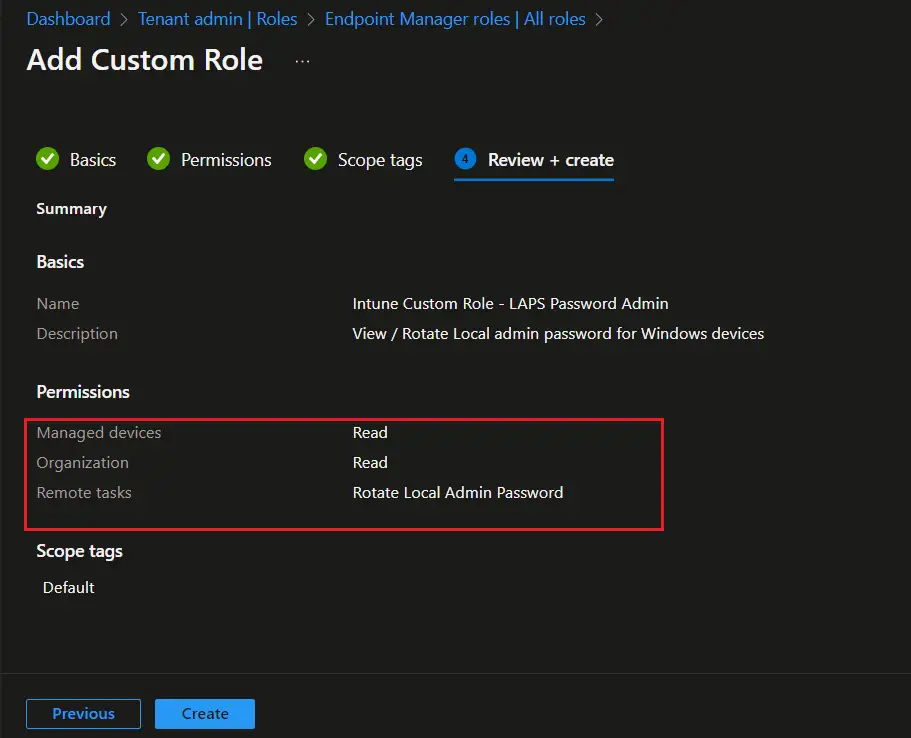
- Manage Device: Read
- Organization: Read
- Remote tasks: Rotate Local Admin Password
- Click on Next
- On the Review + create page, review the details and click on Create.
- The Intune rbac custom role is now created and you can see the same in All roles. Click on the newly created role to assign the role to Azure AD group.
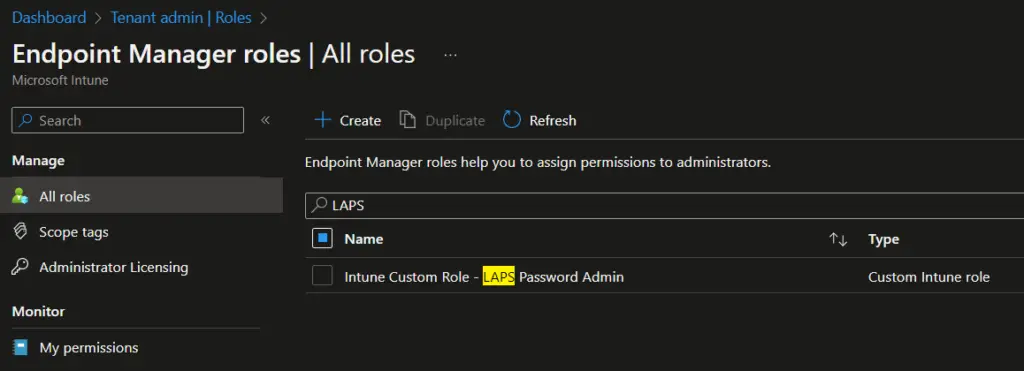
- On the Assignments page, click on Assign link.
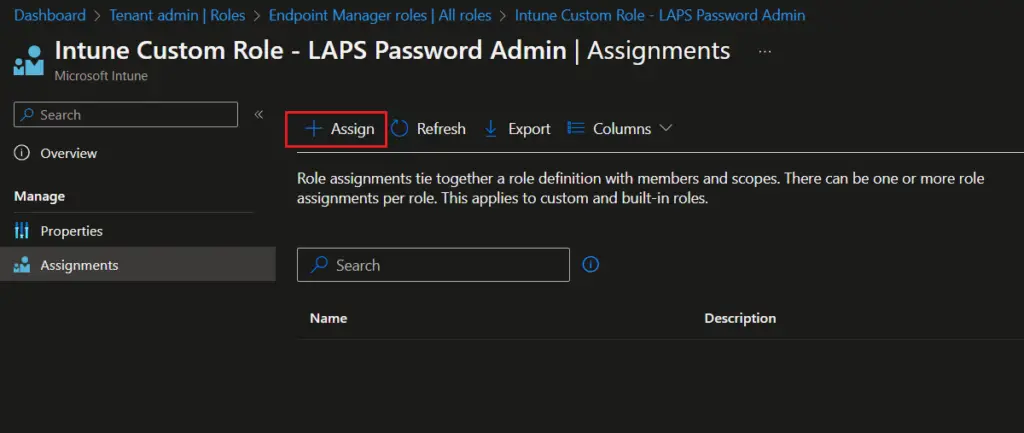
- On the Add Role Assignment > Basics page, provide the name and description for role assignment and click on Next.
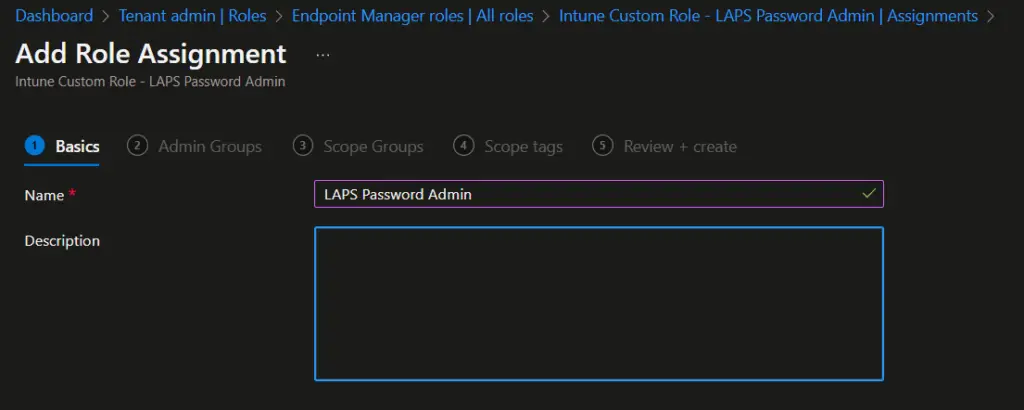
- On the Admin Groups page, click on Add groups and select the AAD group you created for LAPS administrators.
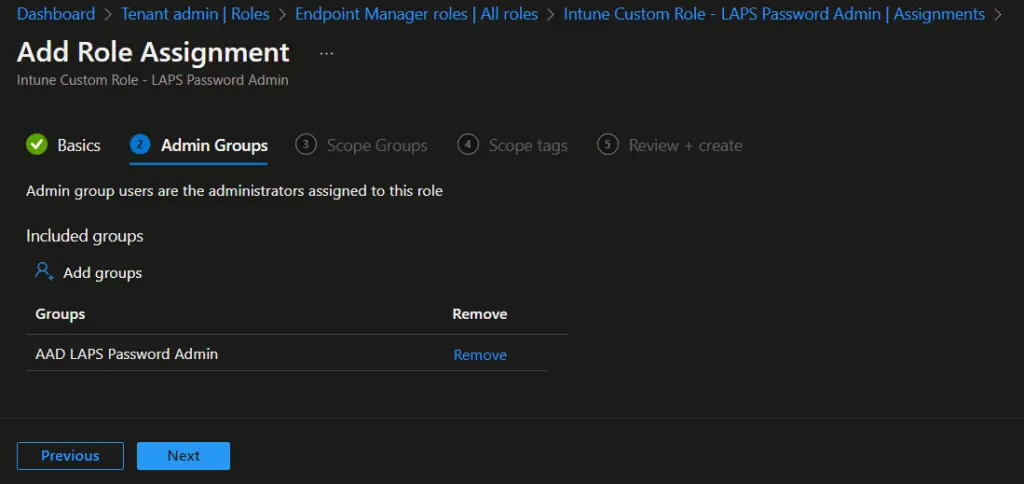
- On the Scope Groups, select All Devices and click on Next.
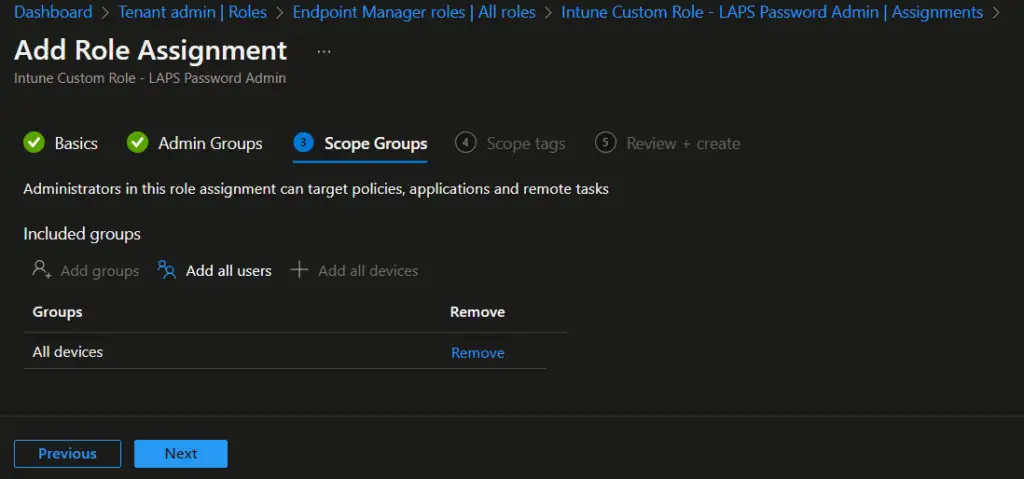
- On the Review + create page, review the settings and click on Create.
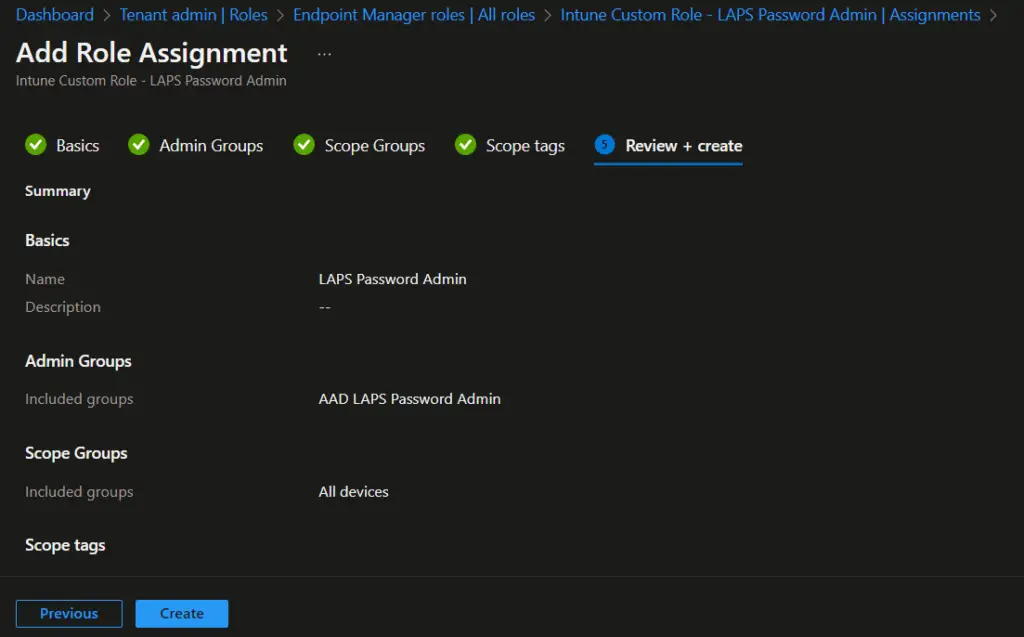
The Intune rbac roles assignment steps are now completed. Users who are part of the Azure AD group can now able to view local admin password for a device. They can also rotate/change the password if required.
LAPS Password Administrators – Experience
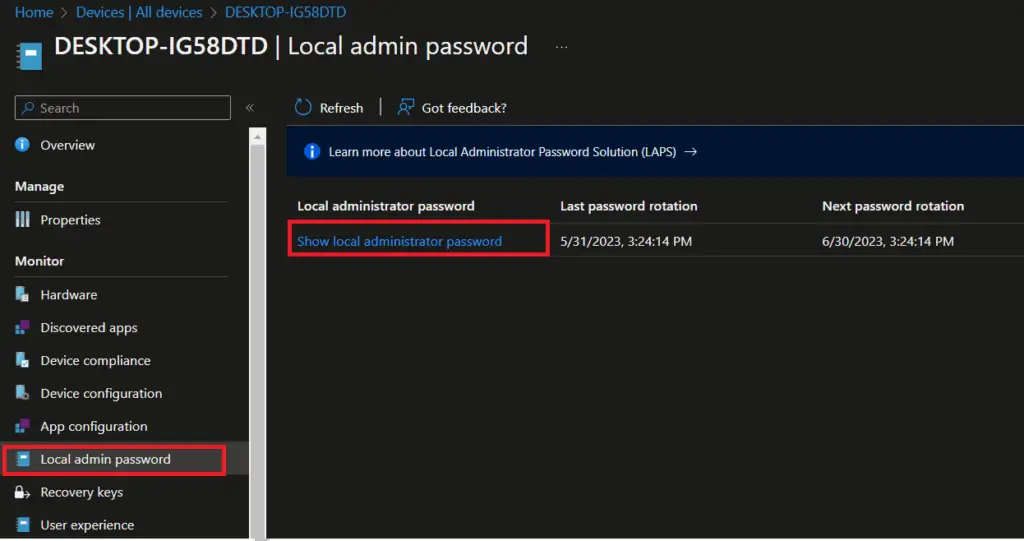
When LAPS Administrator logon to Intune console, they can access Local admin password blade and view local admin password.
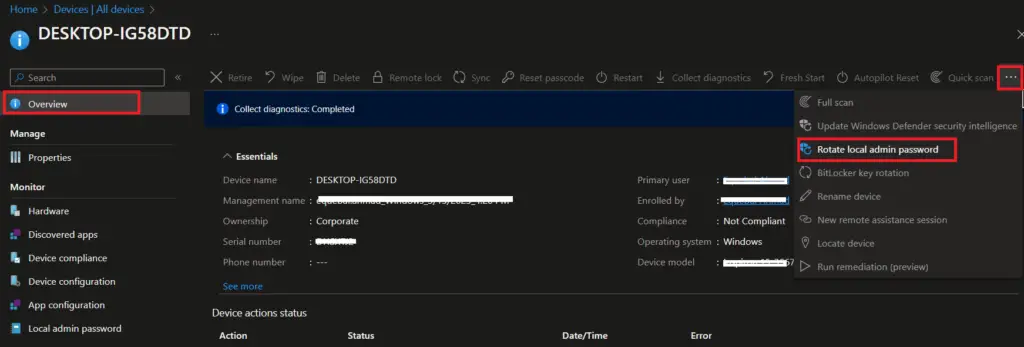
They can also access Rotate local admin password option by clicking on 3 dots at top right. The other options are grayed out in the below screen as we have granted only LAPS password administration privilege to Azure AD group. If the same user is part of other roles, they would be able to perform other actions as well based on the permissions they have.
Related Posts
- Manage Edge Chromium favorites with Endpoint Manager | Intune
- Configure Edge Chromium Homepage & Startup Page
- Configure Microsoft Edge Sleeping Tabs using Intune
- Configure Google Chrome settings using Administrative templates | Intune | Endpoint Manager
- Block USB Device with Exception
- Deny Write Access to USB Devices Using Intune Catalog Settings
- Manage Windows 10 /11 Desktop Wallpaper with Microsoft Intune
- Manage Local Admin Password with Intune & Windows LAPS
- How to Create a Custom RBAC Role in Intune for LAPS Password Administrator
Subscribe to Techuisitive Newsletter
Be the first to know about our new blog posts. Get our newsletters directly in your inbox and stay up to date about Modern Desktop Management technologies & news.