A client certificate is required on any computer which need SSL communication with Configuration Manager HTTPS Management Point or SSL Software Update Point.
A client certificate is aslo required on any computer which will be managed via the Cloud Management Gateway ( CMG ) and devices are not Azure AD / Hybrid AD join. It is also required on the server that will host the Cloud Management Gateway connection point.
Let’s understand how we can issue a client authentication certificate using Microsoft Active Directory Certificate Services (Public Key Infrastructure / PKI) and configure auto enrollment via Group Policy.
Issue Client Authentication Certificate from Microsoft PKI
RDP to Certificate Authority Server
On the Certificate Authority console, right click Certificate Template and click Manage.
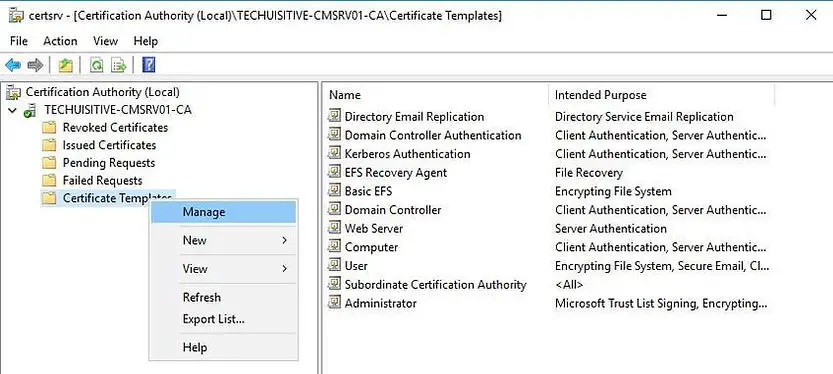
Right click Workstation Authentication and click Duplicate Template.
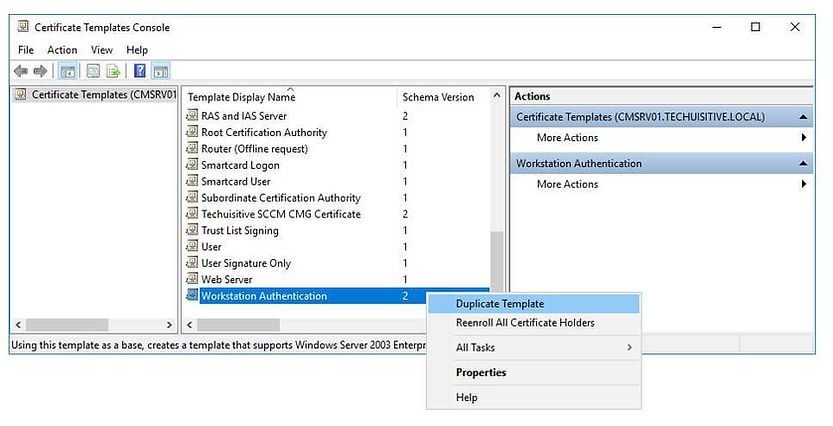
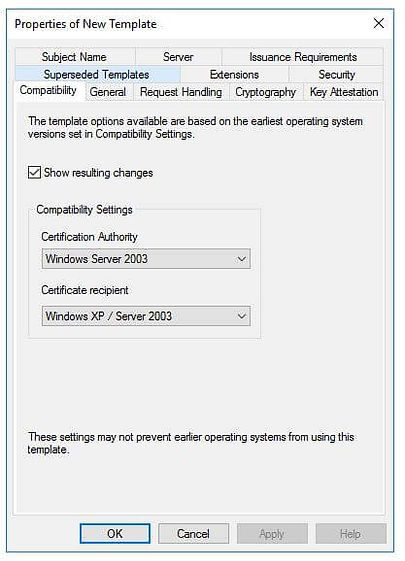
Under Compatibility tab, make sure to use to Windows Server 2003 under Certificate Authority option.
In the General tab, enter SCCM Client Certificate under Template display name. Set the validity period as per your requirement.
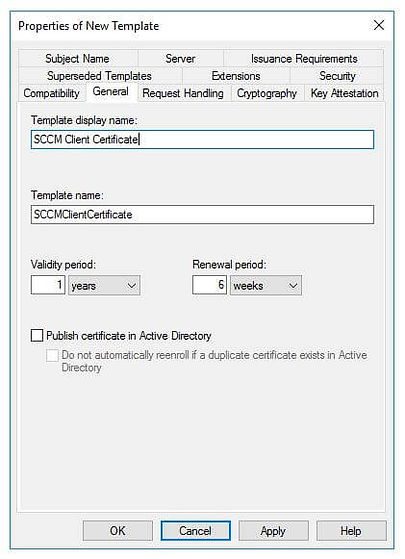
Click on Security tab, select the Domain Computers group and add the permission of Read and Autoenroll , do not clear Enroll. Then click on Ok
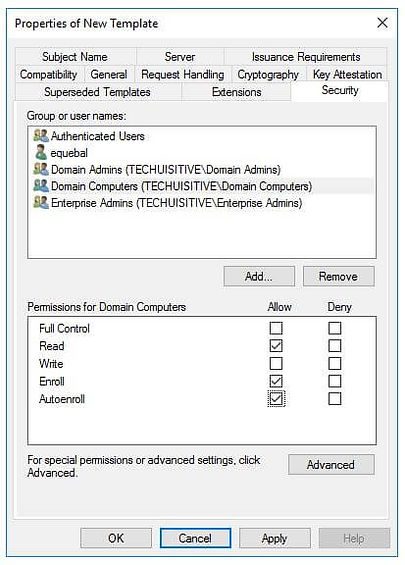
Refresh the console and check if new template is there
In the Certificate Authority console, right-click Certificate Templates, choose New, and then choose Certificate Template to Issue.
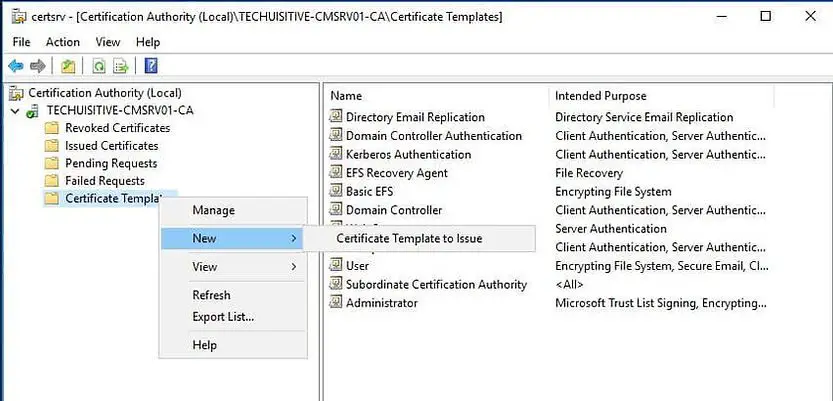
In the Enable Certificate Templates dialog box, choose the new template that you just created, ConfigMgr Client Certificate, and then choose OK.
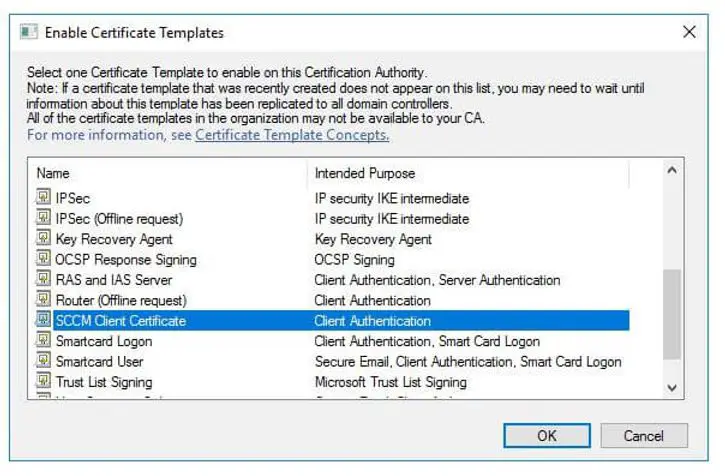
Configure Client Authentication Certificate Auto Enrollment
The fastest way to deploy the client certificate to all your machines is through an autoenrollment GPO. Follow the below process to configure auto enrollment group policy.
Launch Group Policy Management on your Domain (Start / Administrative Tools / Group Policy Management)
Right-click the desired OU and select Create a GPO in this domain, and Link it here…
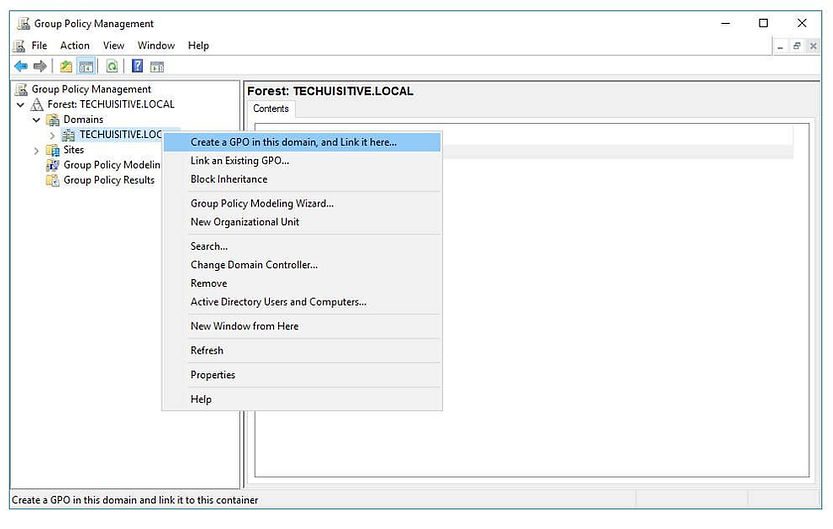
Name your GPO SCCM Client Cert – Auto Enroll, then click OK.
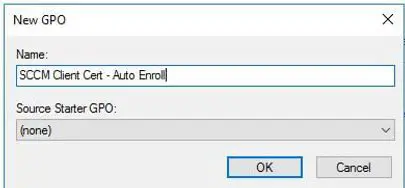
A blank GPO will now created. Right-click and Edit your newly created GPO.
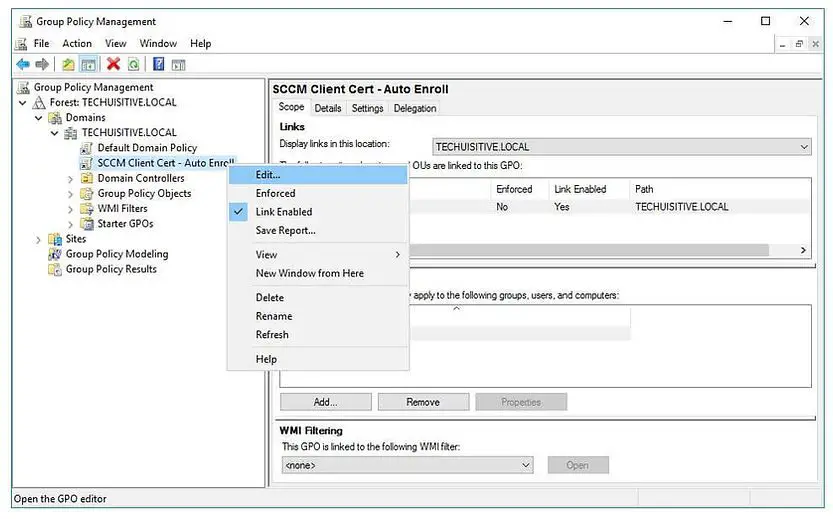
Navigate to: Computer Configuration / Policies / Windows Settings / Security Settings / Public Key Policies
Right-click on Certificate Services Client – Auto-Enrollment and then click Properties
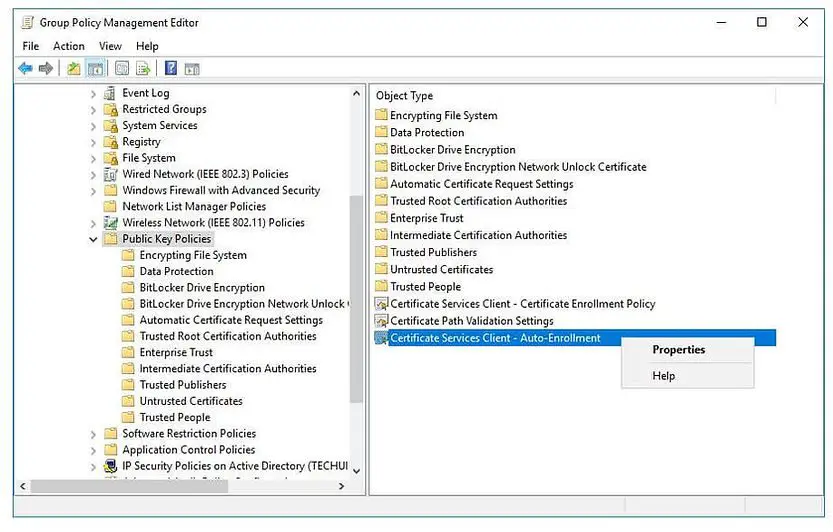
Change the Configuration Model: to Enabled
Select the Renew expired certificates, update pending certificates, and remove revoked certificates checkbox
Click Apply and OK
The group policy is now configured for auto enrollment. When Group Policy is re-applied, any machine on the domain communicating with the Domain Controller will request and recevie a client authentication certificate automatically.
On the client machine, certificate will be placed in the Local Computer Personal Certificate Store
To expedite the testing, you can reboot a workstations and run gpudate /force command to forcefully update the Group Policy.
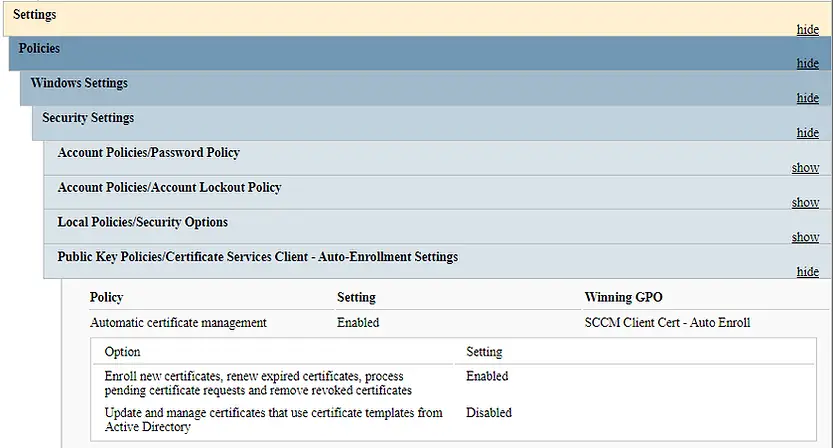
Below is the result from GPRESULT command. You can see that GPO has been applied and SCCM Client Cert- Auto enroll is winning GPO.
Export Trusted Root Certificate
The trusted root certificate need to be provided to SCCM server when configuring for SSL. It’s also required for Cloud Management Gateway during setup.
Follow the below steps to export the trusted root certificate from the workstation which enrolled the client authentication certificate through GPO.
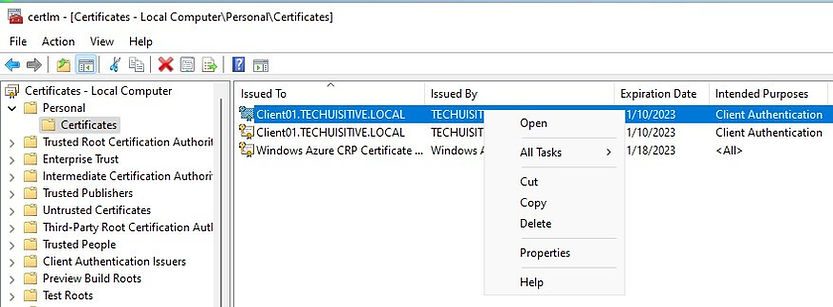
Go to Run and type certlm.msc and press enter to open local computer certificate store.
Right click on the client authenication certificate and select Open
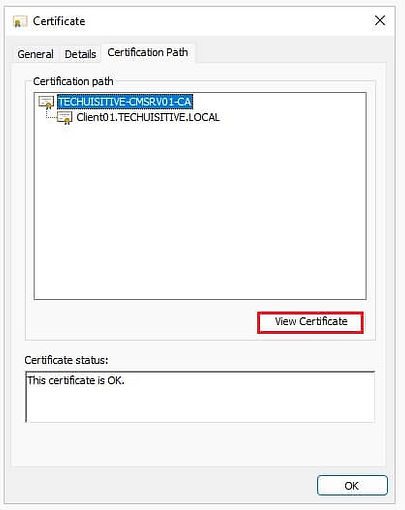
In the Certificate page, select highest certification path and click on View certificate.
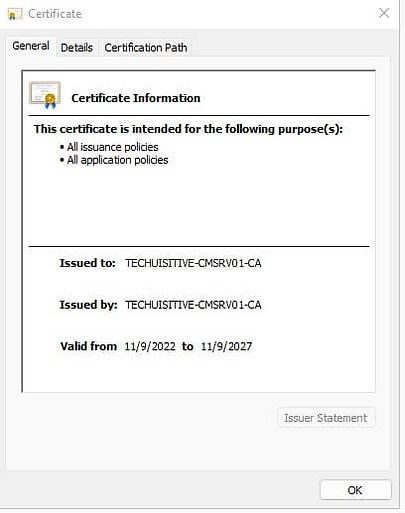
The Certificate Information page will open in a new window
Click on the Details tab and then click on Copy to file…
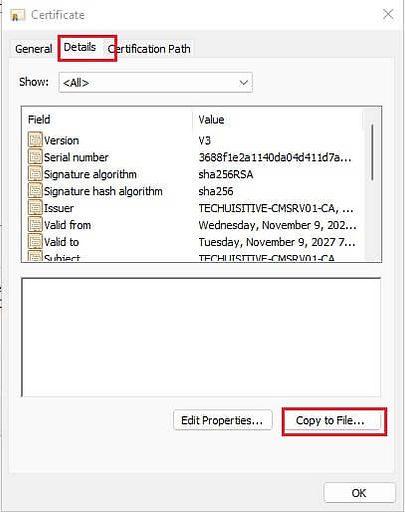
On the Welcome to the Certificate Export Wizard page, click on Next
On the Certificate Export Wizard page, ensure that DER conded binary X.509 (.CER) format is selected.
Click on Next
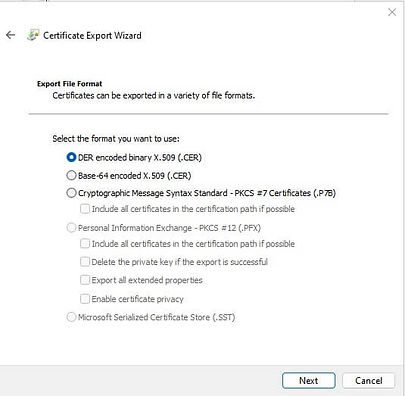
Provide the name for the file and click on Next
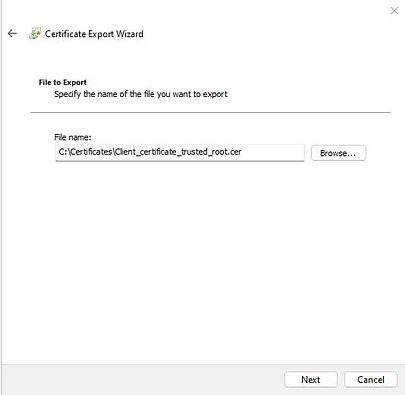
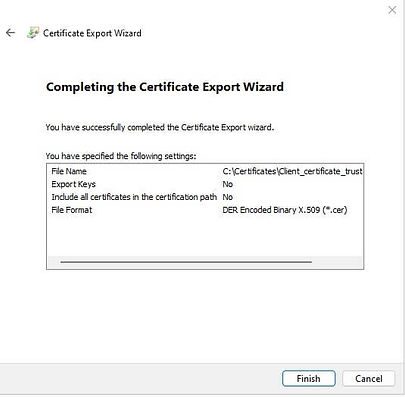
On the Completing the Certificate Export Wizard page, click on Finish.
Related Posts:
- Configure Management Point for HTTPS | ConfigMgr | SCCM
- Configure Software Update Point for SSL | ConfigMgr | SCCM
- Deploy client authentication certificate for SCCM clients
- SCCM CMG Part 1 | Cloud Management Gateway (CMG) Setup Guide
- SCCM CMG Part 2 | Issue, Enroll & Export Server Authentication Certificate
- SCCM CMG Part 3 | Configure SCCM Site for SSL
- SCCM CMG Part 4 | Integrate Azure Active Directory with ConfigMgr
- SCCM CMG Part 5 | Setup Cloud Management Gateway
- SCCM CMG Part 6 | Validate CMG Health & Client Communication
- Location of smsts.log file during Operating System Deployment (OSD)
- Schedule SCCM Client Reboot through ConfigMgr
- Check Software Center Business Hours of Remote Computer
- SCCM Software deployment strategy
- How to deal with wrong deployment in ConfigMgr
- How to Initiate SCCM client agent actions using PowerShell
Subscribe to Techuisitive Newsletter
Be the first to know about our new blog posts. Get our newsletters directly in your inbox and stay up to date about Modern Desktop Management technologies & news.
