In Microsoft Intune Win32 App Detection Rules are used to determine the presence of a Win32 App. The detection rules ensure that app installation only starts if it’s not installed yet. A Win32 App can have multiple detection rules and all detection rules must be met to detect the application. However, in the case of an Uninstall, only one detection rule should match to trigger an uninstall.
In this article, we will discuss different detection rules available in Microsoft Intune for Widows Apps (Win32).
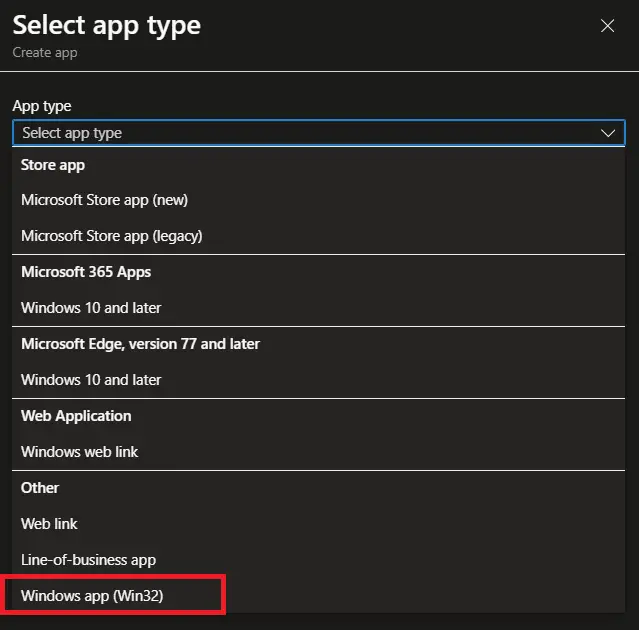
Win32 App Detection Rules
Let’s have a look at the detection rules available in Microsoft Intune. Open Microsoft Intune admin center and navigate to Apps > Windows > Windows apps, Select any Win32 app and click on Properties > Detection rules to open the Detection rules blade.
Note: You have to create a Win32 app if you don’t have any. Check this article if you want to know how to deploy a win32 app.
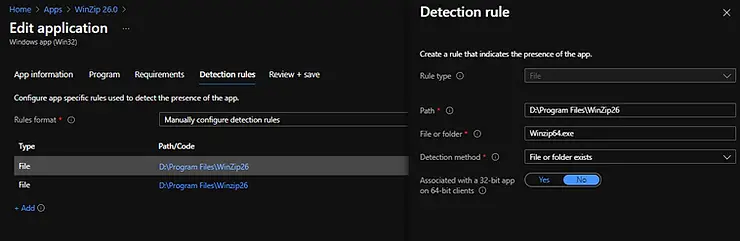
The following detection rule formats are currently available in Microsoft Intune.
Manually configure detection rule: This detection rule format allows the Intune administrator to specify a detection rule based on MSI product code, file or folder existence, file version, registry key, or registry value.
Use custom detection rules: This detection rule format allows the Intune administrator to specify detection rules using a custom script.
Manually Configure Intune App Detection Rule
Let’s understand how to manually configure Intune detection rules in detail. This detection rule format provides three types of detection rules which are MSI , File & Registry.
MSI Product Based Win32 App Detection Rules
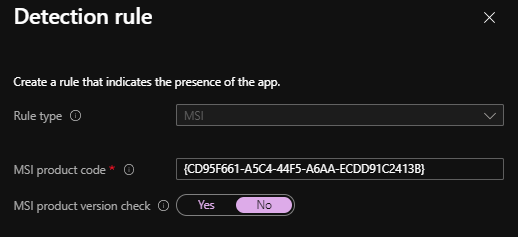
This detection rule detects application installation based on MSI product key or version check. When you choose this rule type, you have two settings:
- MSI product code: This property allows the administrator to configure MSI product code to detect the installation of the App. When you use this rule type with an MSI, the MSDI product key is populated automatically.
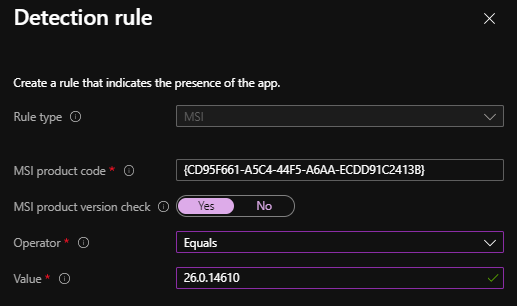
- MSI product version check: This property allows the administrator to configure an additional check that is a specific version of MSI product code to detect the application.
Example of MSI product detection:
Check for app existence based on MSI product code
Check for app existence based on product code and version
Client-side activities:
Each activity of the Win32 app installation process is logged in the Intune Extension Manager log file located in C:\ProgramData\Microsoft\IntuneManagementExtension\Logs folder. That includes downloading policies for detection and installation. We will focus on policy and detection rules in this article.
The below snippets from IntuneExtensionMnager.log show the details of the policy received by a client which includes the details of detection rules.
Get policies = [{"Id":"4c153c53-913e-4a75-92b1-27e53ca03876","Name":"WinZip 26.0","Version":1,"Intent":3,"TargetType":2,"AppApplicabilityStateDueToAssginmentFilters":null,"AssignmentFilterIds":null,"DetectionRule":"[{\"DetectionType\":1,\"DetectionText\":\"{\\\"ProductCode\\\":\\\"{CD95F661-A5C4-44F5-A6AA-ECDD91C2413B}\\\",\\\"ProductVersion\\\":\\\"26.0.14610\\\",\\\"ProductVersionOperator\\\":1}\"}]","InstallCommandLine":"msiexec /i winzip260-64.msi /qn INSTALLDIR=\"D:\\Program Files\\WinZip26\"","UninstallCommandLine":"msiexec /x \"
The Win32 App Detection rules phase records the evaluation of each detection rule. The DetectionType 1 represents MSI based detection rule in the above snippets. You can see further the application detection failed as it’s not installed on the client machine.
<![LOG[[Win32App] ===Step=== Detection rules]LOG]!><time="19:32:56.1219769" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] ProcessDetectionRules starts]LOG]!><time="19:32:56.1229716" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] ProcessDetectionRules Parsing InstallEx...]LOG]!><time="19:32:56.1229716" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] DetectionType 1]LOG]!><time="19:32:56.1239684" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] Start detectionManager SideCarProductCodeDetectionManager]LOG]!><time="19:32:56.1249660" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[CheckProductCodeExists fails with product code {CD95F661-A5C4-44F5-A6AA-ECDD91C2413B}, errorCode = 1605, try without brace]LOG]!><time="19:32:56.1259630" date="2-22-2022" component="IntuneManagementExtension" context="" type="2" thread="21" file=""> <![LOG[CheckProductCodeExists fails with product code CD95F661-A5C4-44F5-A6AA-ECDD91C2413B, errorCode = 87]LOG]!><time="19:32:56.1259630" date="2-22-2022" component="IntuneManagementExtension" context="" type="3" thread="21" file=""> <![LOG[[Win32App] Checked ProductCode {CD95F661-A5C4-44F5-A6AA-ECDD91C2413B}, Cannot find, applicationDetected: False]LOG]!><time="19:32:56.1273728" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file="">
Post-installation application detection
Since the application was not detected during the Detection phase, The application will be offered to the client. The same detection rules will be evaluated again after application installation to confirm the application’s existence on the machine.
<![LOG[[Win32App] ===Step=== Detection rules after Execution]LOG]!><time="19:36:24.5691438" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] ProcessDetectionRules starts]LOG]!><time="19:36:24.5691438" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] ProcessDetectionRules Parsing InstallEx...]LOG]!><time="19:36:24.5701379" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] DetectionType 1]LOG]!><time="19:36:24.5711353" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] Start detectionManager SideCarProductCodeDetectionManager]LOG]!><time="19:36:24.5721336" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] Equal: actualValue: 26.0.14610, compareValue: 26.0.14610, applicationDetected: True]LOG]!><time="19:36:24.5721336" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] detectionManager SideCarProductCodeDetectionManager got applicationDetectedByCurrentRule: True as system]LOG]!><time="19:36:24.5731672" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] Completed detectionManager SideCarProductCodeDetectionManager, applicationDetectedByCurrentRule: True]LOG]!><time="19:36:24.5731672" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file="">
File Based Win32 App Detection Rules
These Win32 app detection rules verify application presence based on file or folder existence, date, version, or size. You have to provide the following details when using this Intune detection rule.
- Path: Enter the full path of the folder that contains the file or folder to detect.
- File or folder: Enter the file or folder to detect.
- Detection method: Select the type of detection method used to validate the app’s presence.
- File or folder exists
- Date modified
- Date created
- String (version)
- Size in MB
A Win32 app detection rule can have multiple File based detection rules. When you have added more than one detection rule for app installation, all rule evaluation results must be true for the application to get detected.
Example of File-based detection:
Check for file existence:
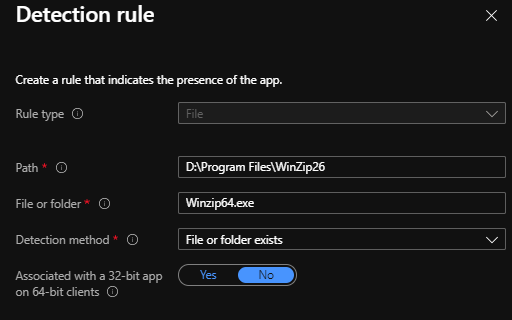
Check for the file version check:

Client side activities:
This article explains that you can view client-side activities in the Intune Extension Manager log. You can see in the logs below that the client downloaded the latest policy from Microsoft Intune. It contains all the details for the application including detection rules which we configured in the Intune portal. The DetectionType 2 represents the File / Folder detection rule.
Get policies = [{"Id":"4c153c53-913e-4a75-92b1-27e53ca03876","Name":"WinZip 26.0","Version":1,"Intent":3,"TargetType":2,"AppApplicabilityStateDueToAssginmentFilters":null,"AssignmentFilterIds":null,"DetectionRule":"[{\"DetectionType\":2,\"DetectionText\":\"{\\\"Path\\\":\\\"D:\\\\\\\\Program Files\\\\\\\\WinZip26\\\",\\\"FileOrFolderName\\\":\\\"Winzip64.exe\\\",\\\"Check32BitOn64System\\\":false,\\\"DetectionType\\\":1,\\\"Operator\\\":0,\\\"DetectionValue\\\":null}\"},
{\"DetectionType\":2,\"DetectionText\":\"{\\\"Path\\\":\\\"D:\\\\\\\\Program Files\\\\\\\\Winzip26\\\",\\\"FileOrFolderName\\\":\\\"Winzip64.exe\\\",\\\"Check32BitOn64System\\\":false,\\\"DetectionType\\\":4,\\\"Operator\\\":1,\\\"DetectionValue\\\":\\\"50.260.14610.0\\\"}\"}]","InstallCommandLine":"msiexec /i winzip260-64.msi /qn INSTALLDIR=\"D:\\Program Files\\WinZip26\"","UninstallCommandLine":"msiexec /x \"{CD95F661-A5C4-44F5-A6AA-ECDD91C2413B}\" /q","RequirementRules":" ........
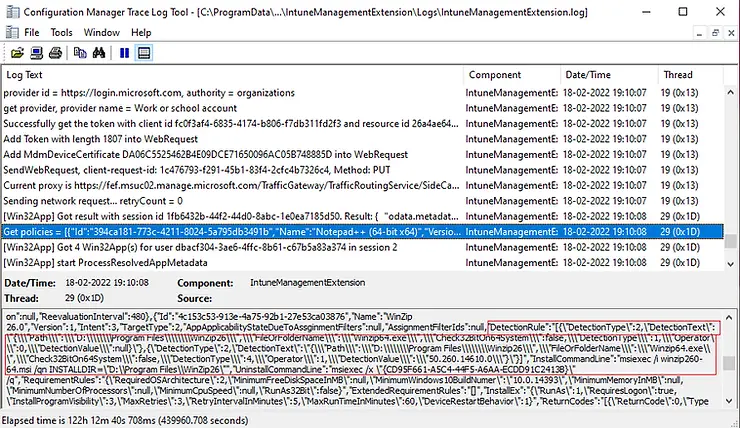
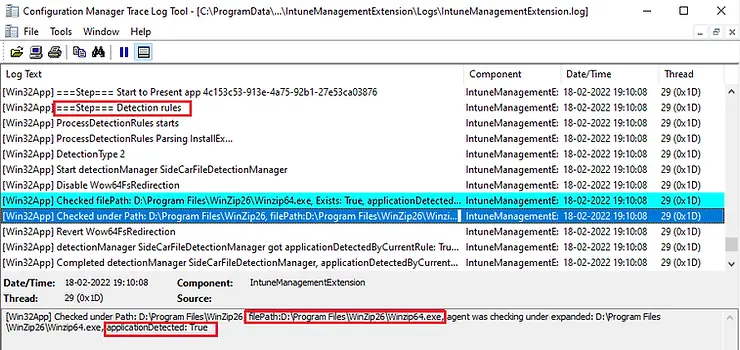
The Detection rules process starts and it checks for the defined rule. As you can see below, we have added two File-based detection rules. The first rule was to check file existence while the second rule was to check file version. The evaluation of both rules must be true for application to get detected as installed. You can see in IntuneManagementExtension.log that it’s checked for file or folder existence rule first.
[Win32App] Checked filePath: D:\Program Files\WinZip26\Winzip64.exe, Exists: True, applicationDetected: True [Win32App] Checked under Path: D:\Program Files\WinZip26, filePath:D:\Program Files\WinZip26\Winzip64.exe, agent was checking under expanded: D:\Program Files\WinZip26\Winzip64.exe, applicationDetected: True
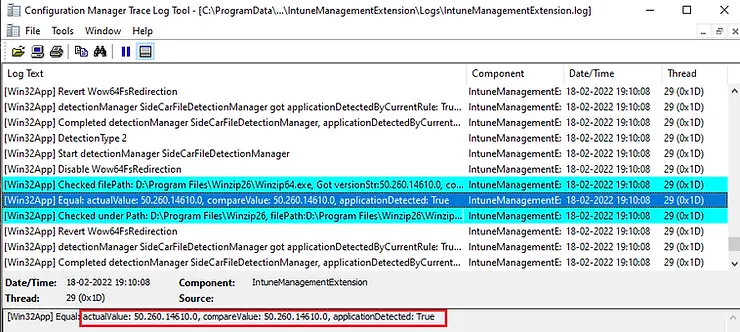
Later, it validated the second detection rule and compared the version installed on the client machine with the version provided in the detection rule. The application will not be offered in this case as both conditions are true and the application was detected on the computer.
[Win32App] Checked filePath: D:\Program Files\Winzip26\Winzip64.exe, Got versionStr:50.260.14610.0, compareValue 50.260.14610.0 [Win32App] Equal: actualValue: 50.260.14610.0, compareValue: 50.260.14610.0, applicationDetected: True [Win32App] Checked under Path: D:\Program Files\Winzip26, filePath:D:\Program Files\Winzip26\Winzip64.exe, agent was checking under expanded: D:\Program Files\Winzip26\Winzip64.exe, applicationDetected: True
Registry Based Win32 App Detection Rules
This registry-based win32 app detection rule verifies the application’s existence based on the Windows registry key, value existence, string, Integer, or version comparison.
- Key path: The full path of the registry key that contains the value to detect.
- Value name: The name of the registry value to detect. If this value is empty, the detection will happen on the key. If the detection method is other than file or folder existence,the (default) value of a key will be used as the detection value
- Detection method: Select the type of detection method that’s used to validate the presence of the app. The following detection methods are available in registry-based detection rules.
- Key exists
- The key does not exist
- String comparison
- Version comparison
- Integer comparison
Example of Registry-based detection:
Please see the Intune registry detection rule example in the below screenshot.
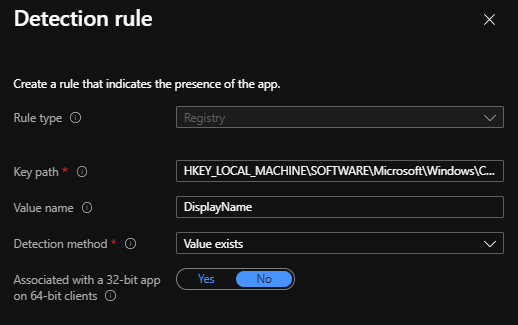
Check for string comparison:
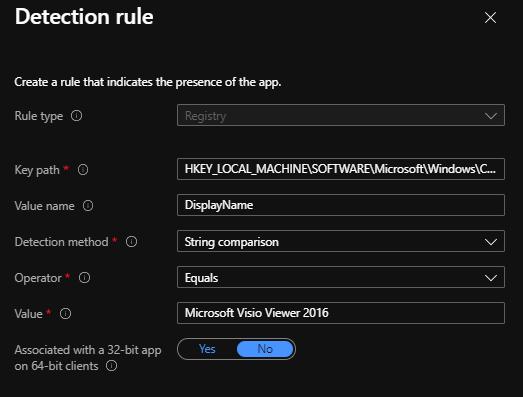
Client-side activities:
Similar to the MSI & File based detection rule, you will see the details of the registry detection rule in the policy downloaded by the client. The DetectionType 0 represents the registry-based detection rule
Get policies = [{"Id":"c9b949c9-6e56-4e3a-a9d5-7f174fd5681c","Name":"visioviewer_4339-1001_x64_en-us.exe","Version":1,"Intent":3,"TargetType":2,"AppApplicabilityStateDueToAssginmentFilters":0,"AssignmentFilterIds":["40a00a67-5909-47bd-8948-54dc237881e6"],"DetectionRule":"[{\"DetectionType\":0,\"DetectionText\":\"{\\\"Check32BitOn64System\\\":0,\\\"Path\\\":\\\"HKEY_LOCAL_MACHINE\\\\\\\\SOFTWARE\\\\\\\\Microsoft\\\\\\\\Windows\\\\\\\\CurrentVersion\\\\\\\\Uninstall\\\\\\\\{95160000-0052-0409-1000-0000000FF1CE}\\\",\\\"KeyName\\\":\\\"DisplayName\\\",\\\"DetectionType\\\":3,\\\"Operator\\\":1,\\\"DetectionValue\\\":\\\"Microsoft Visio Viewer 2016\\\"}\"}]","InstallCommandLine":"visioviewer_4339-1001_x64_en-us.exe /quiet","UninstallCommandLine":"visioviewer_4339-1001_x64_en-us /uninstall /quiet","RequirementRules":"
The client starts processing the deployment once it receives the policy. You can see all activities related to app detection in the below log snippets from the Intune extension manager log.
<![LOG[[Win32App] Start detectionManager SideCarRegistryDetectionManager]LOG]!><time="19:36:29.8759872" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[RegistryKeyOrValueExistsFullPath NOT Check32BitOn64, baseReg HKEY_LOCAL_MACHINE]LOG]!><time="19:36:30.0071701" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[RegistryKeyExistsFullPath opening full path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{95160000-0052-0409-1000-0000000FF1CE}...]LOG]!><time="19:36:30.0121586" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[RegistryKeyExistsFullPath NOT Check32BitOn64, baseReg HKEY_LOCAL_MACHINE]LOG]!><time="19:36:30.0121586" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[RegistryKeyExistsFullPath opening subPath SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{95160000-0052-0409-1000-0000000FF1CE}]LOG]!><time="19:36:30.0121586" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] Got reg value path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{95160000-0052-0409-1000-0000000FF1CE}, name: DisplayName, value: Microsoft Visio Viewer 2016]LOG]!><time="19:36:30.0121586" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] Equal: actualValue: Microsoft Visio Viewer 2016, DetectionValue: Microsoft Visio Viewer 2016, applicationDetected: True]LOG]!><time="19:36:30.0121586" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] Checked reg path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{95160000-0052-0409-1000-0000000FF1CE}, name: DisplayName, operator: 1, type: 3, value: Microsoft Visio Viewer 2016 , result of applicationDetected: True]LOG]!><time="19:36:30.0131559" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] detectionManager SideCarRegistryDetectionManager got applicationDetectedByCurrentRule: True as system]LOG]!><time="19:36:30.0131559" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file=""> <![LOG[[Win32App] Completed detectionManager SideCarRegistryDetectionManager, applicationDetectedByCurrentRule: True]LOG]!><time="19:36:30.0131559" date="2-22-2022" component="IntuneManagementExtension" context="" type="1" thread="21" file="">
Use custom detection script
The Intune app detection rules support use of PowerShell script to detect Win32 app presence. The following details are required for this app detection method.
- Script file: Select a PowerShell script that will detect the presence of the app on the client. The app will be detected when the script both returns a 0 value exit code and writes a string value to STDOUT.
- Run the script as 32-bit process on 64-bit clients: Select Yes to run the script in a 32-bit process on 64-bit clients. Select No (default) to run the script in a 64-bit process on 64-bit clients. 32-bit clients run the script in a 32-bit process.
- Enforce script signature check: Select Yes to verify that a trusted publisher has signed the script, which will allow the script to run with no warnings or prompts displayed. The script will run unblocked. Select No (default) to run the script with user confirmation without signature verification.
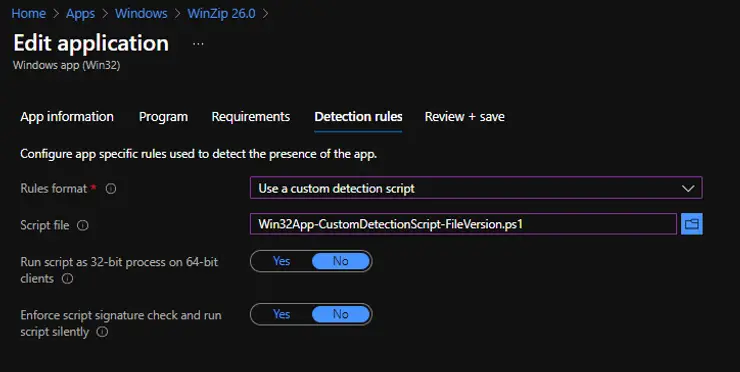
The Intune agent checks the results from the script. It reads the values written by the script to the STDOUT stream, the standard error (STDERR) stream, and the exit code. If the script exits with a nonzero value, the script fails and the application detection status is not installed. If the exit code is zero and STDOUT has data, the application detection status is installed.
Exit Code and STDOUT stream
| Exit Code | STDOUT Stream | Detection State |
| 0 | Not Empty | Detected, Application installed |
| 0 | Empty | Not detected, Application not installed |
| Non zero | Empty | Not detected, Application not installed |
| Non zero | Not Empty | Not detected, Application not installed |
Source: https://www.petervanderwoude.nl/post/working-with-custom-detection-rules-for-win32-apps/
Sample detection script:
Here is a sample script to use with the Custom detection script rule with the Win32 App. The script will check for file existence and its version. It will return Exit code 0 and write a string value in STDOUT if the condition matches. Else, it will return Exit code 0. The Intune extension manager will capture the output written to STDOUT ( using Write-host ) and show that in the log file.
$AppName = "Winzip ver 26.0"
$File = "D:\Program Files\WinZip26\winzip64.exe"
$FileVersion = "50.260.14610 (64-bit)"
Write-Host "Custom script based detection : $AppName"
if (Test-path $File) {
$ActualVersion = (Get-ItemProperty -Path $File).VersionInfo.FileVersion
If ($ActualVersion -eq $FileVersion) {
Write-host "Actual version: $Actualversion, Compared version: $FileVersion"
Write-host "Same version of application installed"
Exit 0}
else {
Write-host "Actual version: $Actualversion, Compared version: $FileVersion"
Write-host "Different Version of application installed"
Exit 0}
}
else {
Write-Host "File $file not found. Application not installed"
Exit 1
}Client-side activities:
Below are the excerpts from the Intune extension manager log. The client downloaded the policy which includes everything about win32 app detection rules. The PowerShell script is also included in the policy in encrypted form. I removed the lines to make it short. The DetectionType 3 represents a custom script-based detection rule.
<![LOG[Get policies = [{"Id":"4c153c53-913e-4a75-92b1-27e53ca03876","Name":"WinZip 26.0","Version":1,"Intent":3,"TargetType":2,"AppApplicabilityStateDueToAssginmentFilters":null,"AssignmentFilterIds":null,"DetectionRule":"[{\"DetectionType\":3,\"DetectionText\":\"{\\\"EnforceSignatureCheck\\\":0,\\\"RunAs32Bit\\\":0,\\\"ScriptBody\\\":\\\"77u/JEFwcE5hbWUgPSAiV2luemlwIHZlciAyNi4wIgokRmlsZSA9ICJEOlxQcm9ncmFtIEZpbGVzXFdpblppcDI2XHdpbnppcDY0LmV4ZSIKJEZpbGVWZXJzaW9uID0gIjUwLjI2MC4xNDYxM2UgeyAKV3JpdGUtSG9zdCAiRmlsZSAkZmlsZSBub3QgZm91bmQuIEFwcGxpY2F0aW9uIG5vdCBpbnN0YWxsZWQiCkV4aXQgMAp9\\\"}\"}]","InstallCommandLine":"msiexec /i winzip260-64.msi /qn INSTALLDIR=\"D:\\Program Files\\WinZip26\"", ........
The below excerpts show the evaluation of the custom detection script.
<![LOG[[Win32App] ===Step=== Detection rules]LOG]!><time="19:10:44.5585753" date="3-1-202x2" component="IntuneManagementExtension" context="" type="1" thread="28" file=""> <![LOG[[Win32App] ProcessDetectionRules starts]LOG]!><time="19:10:44.5585753" date="3-1-2022" component="IntuneManagementExtension" context="" type="1" thread="28" file=""> <![LOG[[Win32App] ProcessDetectionRules Parsing InstallEx...]LOG]!><time="19:10:44.5585753" date="3-1-2022" component="IntuneManagementExtension" context="" type="1" thread="28" file=""> <![LOG[[Win32App] DetectionType 3]LOG]!><time="19:10:44.5595744" date="3-1-2022" component="IntuneManagementExtension" context="" type="1" thread="28" file=""> <![LOG[[Win32App] Start detectionManager SideCarScriptDetectionManager]LOG]!><time="19:10:44.5747007" date="3-1-2022" component="IntuneManagementExtension" context="" type="1" thread="28" file=""> <![LOG[[Win32App] Detection script file C:\Program Files (x86)\Microsoft Intune Management Extension\Content\DetectionScripts\4c153c53-913e-4a75-92b1-27e53ca03876_1.ps1 is saved.]LOG]!><time="19:10:44.7470933" date="3-1-2022" component="IntuneManagementExtension" context="" type="1" thread="28" file=""> <![LOG["C:\Program Files (x86)\Microsoft Intune Management Extension\agentexecutor.exe" -powershellDetection "C:\Program Files (x86)\Microsoft Intune Management Extension\Content\DetectionScripts\4c153c53-913e-4a75-92b1-27e53ca03876_1.ps1" "C:\Program Files (x86)\Microsoft Intune Management Extension\Content\DetectionScripts\4c153c53-913e-4a75-92b1-27e53ca03876_1.ps1quotedResultFilePath.txt" "C:\Program Files (x86)\Microsoft Intune Management Extension\Content\DetectionScripts\4c153c53-913e-4a75-92b1-27e53ca03876_1.ps1quotedErrorFilePath.txt" "C:\Program Files (x86)\Microsoft Intune Management Extension\Content\DetectionScripts\4c153c53-913e-4a75-92b1-27e53ca03876_1.ps1quotedTimeoutFilePath.txt" 3600 "C:\Windows\System32\WindowsPowerShell\v1.0" 0 "C:\Program Files (x86)\Microsoft Intune Management Extension\Content\DetectionScripts\4c153c53-913e-4a75-92b1-27e53ca03876_1.ps1quotedExitCodeFilePath.txt" False]LOG]!><time="19:10:44.8749422" date="3-1-2022" component="IntuneManagementExtension" context="" type="1" thread="28" file=""> <![LOG[[Win32App] SideCarScriptDetectionManager Launch powershell executor in machine session]LOG]!><time="19:10:44.8779350" date="3-1-2022" component="IntuneManagementExtension" context="" type="1" thread="28" file=""> <![LOG[[Win32App] Checked Powershell script result: Custom script based detection : Winzip ver 26.0 Actual version: 50.260.14610 (64-bit), Compared version: 50.260.14610 (64-bit) Same version of application installed ]LOG]!><time="19:10:48.3363923" date="3-1-2022" component="IntuneManagementExtension" context="" type="1" thread="28" file=""> <![LOG[[Win32App] Checked Powershell script exitCode: 1 EnforceSignatureCheck: 0 RunAs32Bit: 0 InstallExRunAs: 1, result of applicationDetected: False]LOG]!><time="19:10:48.3376679" date="3-1-2022" component="IntuneManagementExtension" context="" type="1" thread="28" file="">
If any of the above detection rules are not configured correctly then the application will be offered to the client even if installed. The Intune agent won’t be able to detect the application post-installation. In this case, the deployment will fail with error 0x87D1041C.
Related Posts
- Deploy Win32 App Using Intune Enterprise App Catalog
- Understanding Win32 App Detection Rules
- Understanding Win32 App Requirements Rule
- Upgrade / Replace Win32 Apps with Supersedence Relationship
- Win32 App Deployment with Dependencies
- Win32 Apps vs LOB Apps
- Win32 App Deployment failed with error code 0x80070643
- Win32 App Deployment Failed with Error 0x87D1041C
- Win32 App Deployment failed with error 0x87D300C9
- Win32 App failed with error code 0x80070653
- Deploy Google Chrome for Enterprise with Intune Win32 App
- How to Prepare Win32 App Installation source for Microsoft Intune
- SCCM Device Collection Equivalents in Microsoft Intune for App Deployment
- Deploy Microsoft SQL Server Management Studio 19.02 through Intune
- Organizing Laptop and Desktop in Intune Using Filters
Subscribe to Techuisitive Newsletter
Be the first to know about our new blog posts. Get our newsletters directly in your inbox and stay up to date about Modern Desktop Management technologies & news.